CIO - Job Description - Salary - IT - News
Backup makes disaster recovery business continuity daunting
 BC-DR is daunting. BC-DR requires offsite duplicate data,
infrastructure, storage, systems, networks, floor space, rack space, cables,
power, cooling, etc. Far too many organizations take a look at the cost and
decide they just cant afford it. Per the May 2010 Information Week Business
Continuity Disaster Recovery published survey of the Global 2000 (681
respondents), 37% said they had no current BC-DR plan of which 68% of those said
it was because it is too expensive and too complicated. The better question is
whether they can afford not to have it. It has been proven that 95% of those
organizations that failed to recover their data and systems within two weeks of
a disaster were out of business within two years. This is not a pretty picture.
Regrettably, the consequences of poor BC-DR preparedness will only come to light
when there is a disaster. Up until then, it is a hypothetical risk. Unless an IT
organization has experienced a disaster, they are far more likely to tolerate
the incredible risk.
BC-DR is daunting. BC-DR requires offsite duplicate data,
infrastructure, storage, systems, networks, floor space, rack space, cables,
power, cooling, etc. Far too many organizations take a look at the cost and
decide they just cant afford it. Per the May 2010 Information Week Business
Continuity Disaster Recovery published survey of the Global 2000 (681
respondents), 37% said they had no current BC-DR plan of which 68% of those said
it was because it is too expensive and too complicated. The better question is
whether they can afford not to have it. It has been proven that 95% of those
organizations that failed to recover their data and systems within two weeks of
a disaster were out of business within two years. This is not a pretty picture.
Regrettably, the consequences of poor BC-DR preparedness will only come to light
when there is a disaster. Up until then, it is a hypothetical risk. Unless an IT
organization has experienced a disaster, they are far more likely to tolerate
the incredible risk.
- more info
Not all disasters are equal
Disaster recovery, or DR, is one of those subjects that can be discussed not only at length, but also from many different perspectives. The process of recovering from a storm or other natural disaster that affects people and infrastructure across a wide geographic region is clearly not the same as that required for a business to recover from the impact of, say, a fire at a central warehouse. But no matter at what level one talks about disaster recovery, there are key two metrics, two goals that will inevitably be discussed: the time it takes to recover, to get back to normal, and the state or condition to which one can hope to recover.
These same metrics are central to any discussion of recovery from IT disasters, such as the loss of a server or data center or just the loss of a file or data object. Most commonly, experts in DR planning talk about an organizations recovery expectations in terms of their Recovery Time Objective and their Recovery Point Objective.
Recovery Time Objective (RTO) describes the goal for how quickly data is to be recovered and made available to users after the failure or loss of a system. For example, some companies may be willing to tolerate six to 24 hours of downtime, while others (e.g., large online retailers) are willing to wait only a minute or two.
Recovery Point Objective (RPO) measures the completeness of the data and/or application functionality ultimately recovered. For instance, one shop may be willing to accept the loss (and subsequent manual re-creation) of a days worth of transactions, while another may be willing to tolerate the loss of only transactions that were in process at the very moment the system failed.
- more infoSecrutiy threates increase
Cybercrime continues to evolve and grow in both scale and sophistication. As social networking becomes ever more deeply embedded in our everyday lives, it has become an ever more fertile hunting ground for those who would steal and abuse our personal information, and compromise and misuse our computer systems to gain financial advantage by stealing our personal or corporate funds or obtaining illicit funds from advertisers or spammers.
Just companies have changed their habits to accommodate new technologies and new ways of conducting their everyday business, so security providers have needed to implement new strategies to cope with the massive growth in new malware and new attack vectors.
Keeping track of these continuous and rapid changes is a demanding and complex task, but one that will doubtless be rewarding to the diligent and conscientious. Knowledge is power, and understanding the dangers posed by the modern interconnected world is the first step toward keeping ones identity, possessions and finances safe and secure.
- more infoNet neutrality stalled in Congress
A network neutrality proposal floated by members of the U.S. House Energy and Commerce Committee has stalled.
The proposals would have prohibited wired broadband providers from "unjustly or unreasonably" discriminating against legal Web traffic, but would not apply that prohibition to mobile providers. The bill would have prohibited all broadband providers from blocking consumer access to websites and from blocking legal websites, and it would have prohibited the U.S. Federal Communications Commission from reclassifying broadband as a regulated common-carrier service for two years.
The committee may try to push forward on net neutrality legislation after November's elections, he said, when a lame-duck session of Congress is likely.
- more infoRecent Backup Critical For Disaster Recovery
It has been proven over time that most data recovery requests are for relatively recent data, and that there is a direct correlation between the age of data and the possibility that it would be required for restore purposes. Most restore requests are driven by issues such as an inadvertently deleted file or data corruption that is introduced by a virus or a hacker.
Typically these problems are discovered within several hours or at most a few days from when they first occur, resulting in restore requests for more recent data. In general, the only time you may need to restore data that has already been archived would be in the event of a disaster that physically destroys computer equipment and facilities, such as an earthquake or a tornado. While it pays to be prepared against these occurrences, they are very rare.
The Backup and Backup Retention Policy Template has been used to create customized policies for well over 2,000 enterprises world wide. This policy in concert with the Record Mangement Policy Template are must have Best Practices Tools for CIOs and IT professionals.
For example, factors that CIOs and IT professionals need to consider for backup retention include:
- Business and regulatory requirements - regulatory compliance and data preservation
- Economic and budgetary concerns - doing more with less
- Data loss prevention and information protection - protect, preserve and serve
- Environmental and business sustainment - green and economically efficient
- Maximize IT resource effectiveness and return on investment (ROI)
- Reduce total cost ownership (TCO) of IT resources and service delivery
With the ever changing economic climate and security threats, downtime and data loss pose intolerable risks to every business today. From CIOs to the Executive Suite, managers have seen the importance of business uptime and data protection to continued success, productivity and profitability. The Disaster Planning Template provides a road map to the most effective strategies and technologies to protect data and provide fast recovery should data be lost or corrupted due to accident or malicious action.
- more info26% of All Firms Faced Disaster in Last 5 Years
Janco has found that more than a 26% of its client firms have faced some sort of a disaster over the past five years. CIOs need to convince executives in their enterprise to invest in business continuity and disaster recovery systems. CIO's need to effectively communicate that business continuity and disaster recovery planning is not just an insurance policy.
CIOs know their systems are vulnerable and they want to do something about it. In these tough economic times, it is hard to get funding for business continuity and disaster recovery. CIOs who tie business continuity and disaster recovery planning to mandated compliance needs are more successful in obtaining the necessary funding.
Many of these same companies consider disaster recovery investment as a rolling upgrade that consistently augments existing infrastructure and application investments rather than a one-time event that can be delayed.
In one research study by another firm many CIOs blamed disasters on non-natural disruptions and incidents. The data shows that 42% of the firms surveyed said power failure was the most common cause of declared disasters and downtime, while 32% cited hardware failure, and 21% cited network failure.
- more infoCore security goals for CIOs and IT Managers
CIO and IT Managers need to set minimum security goals for their organizations.
- Know which data they need to secure and protect.
- Have procedures in place for digitizing and storing important information that cannot be retained exclusively in paper format.
- Have lifecycle process Information Technology systems.
- Ensue that business data and records that are no longer needed are securely purged.
- Understand their regulatory and compliance requirements for securing and protecting business data.
- Have file-naming conventions to ensure that secured, protected business data are properly identified.
- Ensures that all staff members know the proper procedures for protecting business information.
- Have automated processes for protecting and backing up data.
- Protect data in secure off-site backup facilities.
- Test their backups to ensure that they are protecting the information that they think that they are protecting.
eCommerce security is basis for customer trust
With the skyrocketing rise in Internet fraud, security of personal data transmissions has never been more critical to e-commerce. The prevalence - and consequences - of identity theft are all too well known and documented. With the increased level of Internet data theft, potential customers have become more savvy, more skeptical, and frankly, more scared. They expect to be protected, and 83% of consumers want more assurance that their information is secure.
Creation of customer trust makes all the difference. Investment in technology to protect customers and earn their trust is trivial when compared to the overall cost of doing business. When the costs are dwarfed by the potential upside, its clear that enhancing e-commerce site security, with technologies like SSL, is an obvious choice for online businesses looking to be successful. To ensure that current and future customers are fully aware of security investments being taken by e-commerce businesses, it is critical to go with a security vendor whose brand name is the best known and the most trusted.
- more infoAvoid IE 9 64 bit Beta – Bug filled and unstable
Janco has just completed its preliminary test of IE 9 64 bit Beta for Windows 7 and has issued an AVOID and DO INSTALL notice to its clients. The CEO of Janco, Vic Janulaitis said, In preliminary testing we found that IE 9 does not render some complex pages the say way as IE 8. In addition some java scripts do not work including doubleclick. He added. This truly is a beta product and should not be installed on any machine that is used for production purposes. In addition the, the install is done via a system update versus program install and requires a re-boot after the installed update is removed.
Janco testing also revealed that IE 9 will require that web developers review all of the design features they have included their web site designs.
- more infoHurrican Earl will test many Disaster Recovery and Business Continuity Plans
When Hurricane Earl, now a major hurricane, hits the East Coast of the U.S. later this week many enterprises will find that their Business continuity plans were not adequately tested.
Critical data centers, with backup generators, facilities and fuel supplies, are now built to continue operating during storms. The same can't be said for the computing setups that telecommuters maintain in their homes, and they may be put to the test this year.
Disaster Planning Base for Business Continuity
Order Disaster Recovery Plan Template Download Selected Pages
Last year there were only three hurricanes in U.S. waters last year, and none of them brought hurricane force winds over land in this country. In 2009, there were an average of 236 power outages a month in the U.S. Through July of 2010, the average had increased to 273 a month.
The need for teleworkers to be self-sufficient (and less dependent on coffee shops and local libraries for wireless access) is growing. In a report released last month, the Metropolitan Washington Council of Governments estimated that there as may be as many as 600,000 workers, or about 25% of the region's workforce, who telework at least one day a week. The council also discovered, via a telephone survey of more than 6,000 area workers, that the number of teleworkers could rise by 500,000 over the next few years.
When blizzards early this year prompted a multiday shutdown of federal
offices, many federal employees rose to the challenge and continued to work,
making good use of telework and other work flexibilities. The question is
will Hurricane Earl be as easy on existing Disaster Recovery and Business
Continuity Plans.
Cloud computing capacity planning is complex
The cloud computing model reduces the need for capacity planning at an application level. An application can simply request resources from the cloud and obtain them in less than an hour in accordance with dynamic demand. Thus, it is far less important to correctly predict the capacity requirements for an application than it is in traditional data centers, for which as many as six months might be needed to order and install hardware dedicated to the application.
 On the other
hand, virtualization makes it harder and more important to plan capacity from
the data centers perspective. In the past, data center managers could use the
projections from applications, take into account the hardware on order, and thus
avoid having to dynamically adjust the capacity of deployed hardware.
Traditionally, a data center would just need to make sure that it had the
capability to support the hardware planned by individual applications. In a
cloud environment, however, many different applications will be installed. It
becomes the data center managers responsibility to predict the average or total
resource requirement of all the applications and to order enough hardware in
advance independently of the input from application owners.
On the other
hand, virtualization makes it harder and more important to plan capacity from
the data centers perspective. In the past, data center managers could use the
projections from applications, take into account the hardware on order, and thus
avoid having to dynamically adjust the capacity of deployed hardware.
Traditionally, a data center would just need to make sure that it had the
capability to support the hardware planned by individual applications. In a
cloud environment, however, many different applications will be installed. It
becomes the data center managers responsibility to predict the average or total
resource requirement of all the applications and to order enough hardware in
advance independently of the input from application owners.
The basis for capacity planning, then, lies in monitoring existing usage and keeping track over historical time periods. Long-term trends can be projected based on previous activity and adjusted without any knowledge of business plans. In a data center-driven cloud, typical capacity planning techniques can be applied for the most part. Since clouds use virtualized resources that share the same physical resources, this makes capacity planning somewhat more complex. In contrast, the capacity planning does not need to consider each individual application, and can simply track and project the overall summation of all applications on the cloud.
- more infoCloud computing gone wrong
A leading software company in the application development and governance
market, made headlines in 2008 when it decided to migrate all of their 600 employees from Microsoft Exchange to Google Apps. After months
of user dissatisfaction, content loss and poor support, the company decided to
make a full migration off of Google Apps to Microsoft's Business Productivity
Online Suite. Since then, user confidence has returned, IT has once again become
a trusted partner, and the company can increase their focus on their core
business.
employees from Microsoft Exchange to Google Apps. After months
of user dissatisfaction, content loss and poor support, the company decided to
make a full migration off of Google Apps to Microsoft's Business Productivity
Online Suite. Since then, user confidence has returned, IT has once again become
a trusted partner, and the company can increase their focus on their core
business.
The Practical Guided for Cloud Outsourcing Template includes -- Sample Cloud Outsourcing Contract along with a Service Level Agreement and other tools to facilitate the cloud outsourcing process. The template includes Janco's exclusive Business and IT Impact Questionnaire.
The template is delivered electronically in WORD and/or PDF format. Included are two 3 page t job descriptions - Cloud Application Manager and Cloud Computing Architect. Sarbanes-Oxley issues are addressed directly, alond with an ISO 27001 and ISO 27002 audit program.
- more infoGoogle Desktop is in a World of Hurt
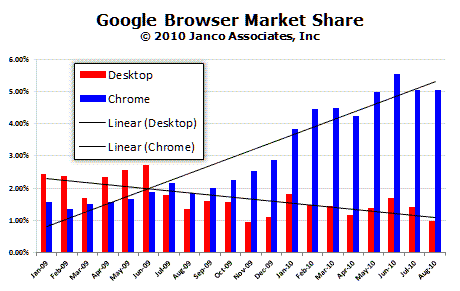
Janco has just released its Browser and Operating System Market Share White Paper. The study shows that in the last 12 months Microsoft's browser market share has continued to erode Microsoft lost over 4% in the last 12 months; Firefox's market share is unchanged for the last 12 months; and Google Desktop and Chrome now have just under 6%. On the operating systems side, Windows 7 is being accepted at a pace is parallel to the way Window XP was in the 90's. The CEO of Janco Associates, Victor Janulaitis said, "The last six months have been a mixed bag for Microsoft. Their browser market share has fallen to level that they back in 1998 with no end in sight. At the same time Windows 7 now has 17% of the OS market in less than 13 months since its availability."
Google Desktop is going the way of Netscape
Google Desktop has not taken off as the emphasis seems to be on Chrome. Based on these trends we belive that unless Google places more emphasis on Desktop, in short order Desktop will no longer be a force in browser market.
- more infoSecurity Breach Impacts 3,000 Bank Accounts
Consumers and businesses in Great Britain have lost more than $1 million so far this summer from a Trojan that is infecting their computers, prompting them to log into their bank accounts, and then is surreptitiously transferring money to scammers in other countries.
About 3,000 bank accounts were found to be compromised at one financial institution, which was not identified, according to a white paper released by M86 Security.
The multilevel scheme uses a combination of a new version of the Zeus keylogger and password stealer Trojan, which targets Windows-based computers and runs on major browsers, and exploit toolkits to get around anti-fraud systems used at bank Web sites, the report found.
Bank sites that offer two-factor authentication, such as one-time passcodes and ID tokens, are ineffective because the malware has taken over the browser after the victim has logged into the banking site.
- more infoLayers of Disaster Recovery Defined
Business continuity can mean success or failure if data and applications on a production server are lost. Disaster recovery planning ensures organizations have the capability to continue essential functions across a wide range of situations that could disrupt normal operations. However, traditional data protection strategies focus on just the data and not the application. Read this white paper for a discussion on how layers of protection not only mitigate the risk of data loss, but also maintain the health and uptime of systems and applications.
- more infoSecurity is poor at many companies
Social engineering hackers -- people who trick employees into doing and saying things that they shouldn't -- took their best shot at the Fortune 500 during a contest at Defcon and showed how easy it is to get people to talk, if only you tell the right lie.
Contestants got IT staffers at major corporations, including Microsoft, Cisco Systems, Apple, and Shell, to give up all sorts of information that could be used in a computer attack, including what browser and version number they were using (the first two companies called were using IE6), what software they use to open pdf documents, their operating system and service pack number, their mail client, the antivirus software they use, and even the name of their local wireless network.
- more infoBasics for business continuity planning
(IBM) - Planning for inevitable disruptions requires an understanding of the essentials of each of these five elements:
 Keep people busy with business as usual
- Planning for employees, business partners and customers makes up the most
critical aspect of business recovery planning. Depending on the nature of the
outage, you may need to figure out how and where people can continue working.
For a brief period of time, everyone may need to work remotely, but youll
need to have these contingency plans ready, along with automatic notification
to tell employees to work at home.
Keep people busy with business as usual
- Planning for employees, business partners and customers makes up the most
critical aspect of business recovery planning. Depending on the nature of the
outage, you may need to figure out how and where people can continue working.
For a brief period of time, everyone may need to work remotely, but youll
need to have these contingency plans ready, along with automatic notification
to tell employees to work at home.- Make accommodations for facilities - Facilities make up an important part of business recovery planning. According to the U.S. National Fire Protection Agency, 35 percent of businesses that experience a major fire are out of business within three years. So, if having everyone work at home is not the best option for your business, recovery vendors can provide interim workplaces such as prefabricated mobile offices or buildings designed specifically for use in times of crisis.
- Secure information before the storm hits - Data can make or break a business - According to the U.S. National Archives and Records Administration, 80 percent of companies without well-conceived data protection and recovery strategies go out of business within two years of a major disaster. Backup tape and storage testing services can help ensure that critical data will be available after a major outage. Ideally backups should be performed offsite, preferably at a facility far away from everyday operations. The best way to protect the information for a small business is to use a remote data backup facility, which actually transmits the data either overnight or at scheduled times to a remote site where it is stored.
- Prepare alternate networking routes - Can you keep networks open - or restore them quickly? What happens if you don't have local area network (LAN) or wide area network (WAN) connectivity for an extended period of time? Or phone connections and e-mail? In the worst-case scenario, your business may not have access to any of these vital services. LAN and WAN contingency plans can include services such as remote data access so critical information can be managed and administered from any location. A failover system for e-mail is also highly recommended by Sirota, who notes that keeping in touch with partners and customers can make all the difference in remaining in business. These solutions can be activated in seconds, but keep in mind that these systems need to be in place prior to an outage.
- Keep technology up-to-date and aligned with recovery plans Keep tabs on how technology is applied within your organization - This can be as simple as making sure a security patch has been correctly applied. Otherwise, recovery plans can be easily derailed when new software and hardware is added or upgraded without testing the potential consequences of changes to business technology. That's why experts recommend routine system checkups, as well as longer-term business continuity and resilience planning services. Resilience is the ability to take a blow and keep on going.
Social networking policy is a must
Social networks are about radically transforming the traditional battlefield of marketing and PR. Your social networking policy, in turn, is the rule book that defines the guidelines used to wage and win this war of the new media. While beginners new to the scene might mistake the presence of a policy for social networking as nothing more than a protective mechanism, the truth is that it exists not to limit but really to liberate participants.
Applied properly, the strategic use of social networks will allow a David to outmaneuver and outrun Goliaths, or for heavyweights to propel their reputation and brand awareness to greater heights. As social media gurus have said, The unique characteristics of disembodied identities in the virtual world can radically transform rules that traditionally govern social groups.
This is evidenced in the way large corporations are hiring digital or social media managers, or incorporating such roles into the primary job responsibilities of existing PR or marketing executives. As companies strive to cash in the rewards of successfully engaging social media, guidelines are required to formalize a company's strategy in this new, uncharted terrain. In addition, there is a need to recognize and protect social media practitioners within the company.
Taken together, it is clear that there is a need to craft a proper social networking policy so as to maintain a degree of consistency in your organization's engagement of social media. So what does a social networking policy consist of? The quick answer might be to point you toward a sample of a simple social networking policy on e-janco.com.
- more infoFocus of CIOs shifting
As the economy moves towards recovery, CIOs need to develop new strategies to be successful in the every changing business environment. This new strategy need to be structured around the following business imperatives.
- Technology solutions need to be flexible and focused on IT Service Management and Service Oriented Architecture. Businesses must be able to respond to opportunities and challenges faster than ever before. Businesses are battling other well-resourced organizations that may be based where the opportunity originated, lower cost market, or another company that is reaching out for new opportunities. In order to compete, businesses have to be able to rapidly deliver products or service as good, or better, than that of any other company.
- Complexity should be avoided - infrastructure is key. Simplicity has always been rewarded, as the scope of technology increased this has led to increased complexity and risk. While per unit costs of technology typically are decreasing, in aggregate IT and technology cost are increasing. With the pressure on IT to act less as a cost center and more as a way to increase the profitability of business units, just adding more storage, more bandwidth, or additional technologies throughout the organization is no longer viable. Instead, successful CIOs are investing in technologies like continuous data protection, virtualization, and wireless connectivity to help IT slim down its footprint while increasing their businesss competitive advantages.
- Mandated requirements have moved security to be a top priority. With the growing importance of digital applications and data, the sources of threats to enterprise data have multiplied dramatically. Everything from natural disasters to criminals to corrupt sources within the company might try to steal or corrupt data. While businesses do everything that they can to stop these threats in the first place, they still must be prepared to recover from these threats as quickly as possible.
- Business Continuity and Disaster Recovery plans are no longer optional. As businesses have expanded the need for anytime, anywhere application access has become a requirement. At the same time, global 24/7 operations have shrinking maintenance windows and a need for applications to be running at all times. Delay or loss of data for any reason system failure, natural disasters has a domino-like effect across the entire organization, at any time of the day or night.
Steps to Take Before Disaster Strikes
Business continuity and disaster preparedness tips that businesses need to implement immediately.
-
Validate
 that
police and other first responders can contact the right people in your
business - Research the Reverse 911 program for your area and
register your business cell phones, voice over IP numbers or pagers. In an
emergency situation, Reverse 911 enables emergency officials to send out an
automated call to everyone registered in a specific area with important
information.
that
police and other first responders can contact the right people in your
business - Research the Reverse 911 program for your area and
register your business cell phones, voice over IP numbers or pagers. In an
emergency situation, Reverse 911 enables emergency officials to send out an
automated call to everyone registered in a specific area with important
information. -
Program emergency numbers into business cell phones - Save emergency phone numbers for local police and fire departments into your cell phones.
-
Create a business phone tree - Each office should have a plan for contacting employees during emergencies through a designated phone tree. Designated staff should have copies of the phone tree and be trained on who they should call. Management should review and update the phone tree quarterly and conduct regular training sessions. Management should also have back-up copies of employee phone numbers and their emergency contacts. This information should be regularly updated.
-
Register your employee's business cell phone number - Individual employees should make sure family; friends and co-workers have their business mobile or BlackBerry numbers. Each person should register their business cell phone on https://www.WhitePages.com/. This will give colleagues and family members the ability to quickly find the information should they not have it on hand.
-
Have emergency kits accessible - Companies should organize and maintain emergency kits in several places. There should be designated staff responsible for grabbing these in the event of an emergency. Make sure it contains a minimum of provisions for at least three days. Include fresh water, non-perishable food, a manual can opener, blankets, extra clothing, a first-aid kit, matches, a flashlight, a battery-operated radio and extra batteries. Test or replace the batteries at least once a year, especially for smoke alarms.
-
Create back-up copies of documents, data files, and software - At work, keep back-up copies of your important personal and financial statements, and health and property records. Be sure to store important original paperwork in a safe and secure location. This way, you can grab it all quickly in the event of an emergency.
-
Have cash available - Set aside an emergency fund of cash or traveler's checks or both. Keep them in a safe, accessible spot in case of the need for evacuation. Banks and ATMs are often inaccessible during catastrophes.
-
After the disaster have employees register with the American Red Cross - Register with the Red Cross's Safe and Well Web site. If you have been affected by a disaster, this Web site provides a way for you to register yourself as "safe and well."