Browserand Operating System Market Share
White Paper - Firefox - IE - Google Chrome - Mozilla - Vista - Windows 7
Order Browser & OS White Paper Download
Browse rand Operating System Market Share - The Browser Market Share White Paper data is by month starting in September 1997 through the April 2011. Google's market share of the browser market has improved as more users get to know and like Chrome. Below are some graphics from earlier versions of the Browser and OS Market Share Study.
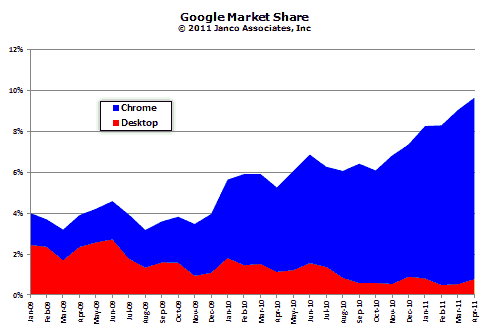
Google market share growth history
Browser Market Share Changes April 2011 - April 2010
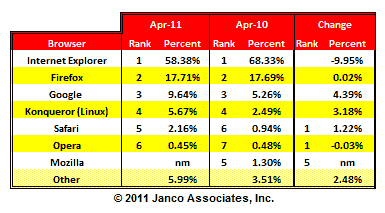
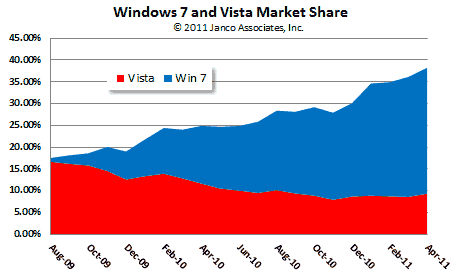
The full study was produced with data through April 2011. The full report contains charts in jpg format and data by month and quarter for each browser.
Janco’s has collected consistent data on browser activity since September 1997. The data is collected from commercial sits which a focus on business to business activity. Janco has over 350,000 data points as it continues to expand it client base. Janco anticipates that it will issue an update to it market share data at the end of the fourth quarter of this year.
The full report contains all of these charts in jpg format and data by month and quarter for each browser in an excel spreadsheet.





