CIO, CTO, CSO, IT Service Management, IT Job Description, Sarbanes Oxley, and IT Salary News
CIO - CTO - CSO News
ASEAN growth of IT will slow
The growth of the technology industry in ASEAN in 2014 will likely mirror that of the region's GDP that is, it will lack intensity and vigor as CIOs continue to face pressure to cut technology management costs. Despite the less-than-rosy outlook, technology priorities such as big data, analytics, and mobility are becoming more critical in ASEAN. These priority shifts reveal the deeper undercurrent that has pervaded the technology landscape in the region: Businesses have entered the customer-obsessed era and CIOs have to adjust to new business demands accordingly.
Janco provides an overview of planned technology budgets and top technology priorities in ASEAN in 2014 based on data from the Forrsights Budgets And Priorities Survey, Q4 2013, which surveyed CIOs and other technology decision-makers in four major ASEAN economies: Indonesia, Malaysia, the Philippines, and Singapore. CIOs in ASEAN can use this analysis to evaluate whether they have sufficiently and strategically positioned themselves in the age of the customer.
- more info
Wireless Hotspost - Best Practices
Employment Digest
Latest Job News
- more info
- 10 BYOD Best Practices for CIOs BYOD Best Practices for CIOs Bring Your Own Devices (BYOD) is exploding all over corporations. CIOs are in the cross hairs and need to follow...
- IT Hiring Picture Improves IT Hiring Picture Improves One in five chief information officers, based on Janco s interviews with U.S.-based chief information officers, anticipate hiring lower-level staff for...
- Released Internet and Information Technology Position Descriptions HandiGuide, Internet and Information Technology Position Descriptions HandiGuide, Janco has released the Internet and IT Position Descriptions HandiGuide® which is over 700 pages; includes...
- Top 10 CIO Leadership and Management Traits CIOs and IT Managers who are successful have some common leadership and management traits Are one of the people and able to get their hands...
- CIO and IT blind spots identified CIO blind spot A new study on The Future of the CIO and Corporate IT 2013-2017 found that senior executives want to increase in employee...
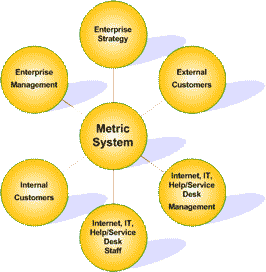
Metrics and Quality Control
World Class IT Organizations and CIOs
Reduced complexity is key element world-class IT organizations use to eliminate nonessential spending, maximize staff productivity and drive down costs. The Janco Associates, Inc. (www.e-janco.com) measures complexity in a couple different ways, one of which being asset and type counts.
When Janco looks at the companies they benchmark, they look at 'type counts. Types of languages, types of data centers, types of software. Janco then can measure how many systems CIOs have to support vs. how much they have to deliver. The more complex an organization, the harder it is to change and respond to changing business needs, and that makes businesses slower, less efficient, and more costly.
CIO Issues
Priority Setting
Compliance Role
Ways to control costs
Tape vs Disk
Improving Productivity
Omni Commerce Best Practices
CIO Career
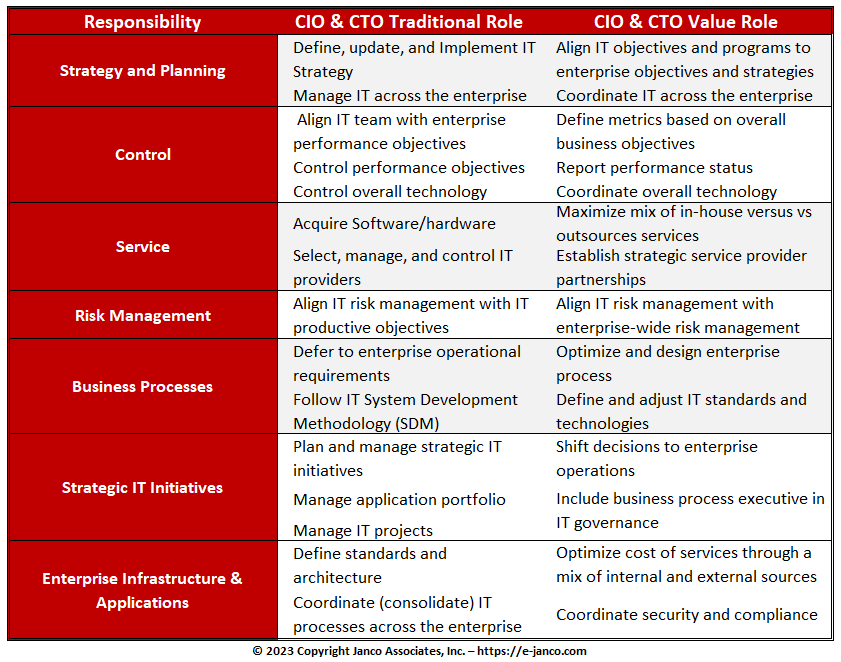
Changing Roles
- more info
Length of Employment
Top Paid CIO
Why CIOs and IT Managers are Terminated
Balanced Scorecard is an implemention is for CIOs
Metrics, Quality, and Cost Control
Have You Implemented the Balanced Scorecard? What has been your experience implementing the balanced scorecard? Have you been able to quantify benefits? What do you think of the framework?
Delivering quality IT service and measuring IT's performance cost effectively is a difficult and time consuming exercise. Many enterprises believe that they do not have the time, money, or resources to initiate and monitor the necessary processes. However, enterprises cannot determine how much something is worth unless its value can be quantified. It is a necessity of the new economy that every business unit needs to demonstrate its worth while meeting necessary service objectives.
- more info
- Business and IT Impact Questionnaire (Risk Assessment)
- Cost Control and Metrics Bundle
- ITIL Template
- Metrics for the Internet, Information Technology, and Service Management
- Quality Assurance and Control Bundle
- Service Level Agreement Template with sample metrics
- Threat and Vulnerability Assessment Tool
WiFi ok for flights
After initially endorsing the use of electronic devices strictly for the content stored on them, a Federal Aviation Administration (FAA) advisory panel has determined that Wi-Fi will be safe to use on an airplane during takeoff and landing, the Wall Street Journal reports.
A member of the FAA committee behind the ruling and the vice president of global public policy for Amazon, said "the vast majority" of airplanes will be "just fine" regardless of the use of Wi-Fi-connected devices on board, according to The Verge.
One interesting aspect to note is that cellular connections are likely to remain restricted, according to the reports. But how will the airlines police that? While many users are likely to connect to a Wi-Fi network when it's available, plenty others won't even think of it. I can't imagine flight attendants checking every device's homescreen for 3G or 4G logos. If cellular network usage is still considered a threat to the planes' communications systems, it remains to be seen how the airlines prevent them from being used during takeoff and landing.
- more info
Best Practices Digest
Best Practices Digest - Recent Articles
- more info
CIO Article Digest
- more info
- Top 10 CIO Productivity and Budgeting Issues CIO Productivity Kit The best companies, and their CIOs, recognize the importance of ready access to the right information to drive the right choices...
- ERP Job Descriptions ERP Enterprise Resource Planning Job Description Bundle Released Janco has just released 15 Enterprise Resource Planning Job Descriptions in its ERP Job Description Bundle. ...
- Many CIOs have not addressed cloud security issues Less than 50% of all organizations have policies in place that for vetting cloud computing applications for possible security risks before deploying them. The number...
- Budgeting Puts Fear Into Many CIOs and IT Managers Budgeting for 2014 is challenge for many CIOs Budgeting can be a harrowing experience or an opportunity to show that you are an executive who...
- IT hiring CIOs have mixed feelings on Fourteen percent of U.S. chief information officers (CIOs) surveyed recently plan to expand their IT teams in the second quarter of 2013, according to a...
Cell Phones are easily hacked
IT security managers should pay attention to such risks and ensure that cell phones that connect to the corporate network have multiple layers of protection, including encryption of data at rest and in transmission
Femotcell technology, used by phone companies to boost cell phone coverage, can be hacked to intercept cell phone calls, text messages and other data. Femtocells are small, low-power base stations provided by phone companies to extend cellular coverage, especially inside buildings and facilities with spotty coverage. The devices use cable or DSL services to connect to a service providers' network.
Researchers from iSec Partners, used an femtocell from Verizon to demonstrate how hackers can eavesdrop on phone conversations and see text messages and photos sent or received by nearby cell phone users.
The researchers gained root access to the Linux operating system used in Verizon's femotcell by interfacing with the device via an HDMI port at the base of the system. Then they used the root access to tweak the femtocell to intercept voice and text messages from cell phones connected to the device.
Verizon has patched the flaw in its femtocells after it was notified. But they added that femtocells from other vendors are vulnerable to the same kind of exploits.
- more info
Firewalls may be at end of life
The U.S. Defense Department is building a single security architecture that ultimately will eliminate firewalls in the future, according to the USAF's Defense Information Systems Agency (DISA) director.
The future architecture, the plans for which are not yet set in stone and will likely change, the general cautioned, will be designed to protect data rather than networks. In the past, weve all been about protecting our networks - firewall here, firewall there, firewall within a service, firewall within an organization, firewalls within DISA. Weve got to remove those and go to protecting the data. You can move that data in a way that it doesn't matter if youre on a classified or unclassified network, depending on someones credentials and their need to know, he declared.
"We want to be able to normalize our networks to where you can have the collaboration and information moving over our networks and you dont have to have the different firewalls, the separate networks, to get those things done," he added. Additionally, the department can realize significant savings in instrumentation - for example, by moving from hard phones to soft phones," he said.
The director stressed the importance of getting the information to the soldier, sailor, airman, Marine, Coast Guardsman, wherever it is they may be.
The single security architecture will improve command and control capabilities, including cyber command and control, he said.
He also discussed the importance of cloud computing. The Defense Department is in the infant stage of deciding how to build the cloud and whether to use a private, public or Defense Department-owned cloud. "We want to do that in fiscal year 14 so that all of this can be automated, and were working feverishly to get that done," he said.
- more info
Disaster Recovery Plan versus Business Continuity Plan
Both the disaster recovery and the business continuity plan covers how employees will communicate, where they will go and how they will keep doing their jobs. The details can vary greatly, depending on the size and scope of a company and the way it does business. For some businesses, issues such as supply chain logistics are most crucial and are the focus on the plan. For others, information technology may play a more pivotal role, and the BC/DR plan may have more of a focus on systems recovery.
The critical point is that neither disaster recovery nor business continuity issues can be ignored. These IT and human resources plans cannot be developed in isolation from each other. The core of disaster recovery and business continuity is about constant communication. Business leaders and IT leaders should work together to determine what kind of plan is necessary and which systems and business units are most crucial to the company. Together, they should decide which people are responsible for declaring a disruptive event and mitigating its effects. Most importantly, the plan should establish a process for locating and communicating with employees after such an event. In a catastrophic event (Hurricane Katrina being a relatively recent example), the plan will also need to take into account that many of those employees will have more pressing concerns than getting back to work.
- more info
IT spending continues to be impacted by business climate
Despite slow economic growth, CFOs expect steady and conservative IT spending going forward in 2013 and and 2014 plans, according to a new survey of CFOs.
A recent study found that 60 percent of CFOs see the economy as similar to that of 2012 with 27 percent seeing an expansion but just not at the level of 2008. For the longer term, 13 percent expect the economy to stabilize at current levels compared to only 1 percent who see growth beyond what they achieved in 2008.
About 39 percent of respondents predicted a similar IT operating expense budget in 2014 as in 2012, while 44 percent forecast an increase and 17 percent see a decrease. For IT capital appropriations, 32 percent project a status quo on spending compared to 48 percent who expect an increase and 20 percent who forecast a decrease.
Business applications and intelligence ranked as more important than technology and social media.
Among CFOs, 27 percent saw the need for IT investment in business applications, 25 percent in business intelligence-related technologies compared to 5 percent in mobile technologies and 2 percent in social networking.
When asked about the top technologies that should be applied in the office of finance today, reconciliation management, financial statement generation/disclosure management and Governance, risk and compliance management solutions ranked among the top five in the survey of CFOs.
- more info
Articles - What Makes a good CIO
- more info
Recap Cloud Solution Articles
- more info
Good job descriptions are key to job satisfaction
At the moment, CIOs may feel like the most highly skilled of IT professionals have a distinct advantage over them in terms of negotiations for compensation, perks and other recruitment enticements. And perhaps that's true - for now.
Great job descriptions are a crital to maintaining good employee morale and focus on long term staff development.
But here's an interesting revelation from the same tech workers who currently possess all the leverage: They harbor significant reservations about the future, according to a recent survey. In fact, a great many of them worry about whether they'll even be able to enjoy a long-term career. They feel the fast pace of IT will eventually render them obsolete, while others sense a workplace bias that favors younger employees. In either case, CIOs may want to reassure valued, veteran IT staffers, and even encourage more training so these employees continue to make impactful contributions. By the same token, IT professionals [must identify] which technologies will become increasingly important at their organizations, and ensure that they are equipped with the skills needed to handle new technology initiatives.
- more info
BYOD is biggest technology shift in the last 20 Years
It's the biggest shift in IT in years: the consumerization-of-IT trend that gained major traction with the advent of the iPhone and other modern mobile devices, causing most businesses to let employees bring -- or at least choose -- their own smartphones and tablets, all in fewer than two years.
The consumerization and BYOD trends are only getting stronger, as success on the mobile front puts pressure on IT to allow other employee-driven technologies, such as PCs, cloud services, desktop apps, and social media.
- more info
IT Departments do not trust BYOD users
In most discussions of Bring Your Own Device (BYOD) and consumerisation the IT departments mistrust of users is evident. Typically, IT departments are not keen on people bringing their own devices into work with the expectation that apps, services and support will just magically work.
But some organisations have decided to trust the user and claim big savings in productivity by deploying BYOD.
- more info
IT Infrastructure Links
Other sites that contain IT Infrastructure information and data that are managed by Janco are:
- www.ejobdescription.com - Policies, procedures, job descriptions and other information related to the human resource aspects of the information technology function.
- it-toolkits.com - Policies, procedures, tools and other information which can help CIOs, CTOs, CSOs, and IT managers to more effectively manage the information technology function.
- www.psrinc.com - A resource site for Information Technology management. This site contains the tools that the CIO, CSO, and CFO can use for Sarbanes Oxley, Disaster Recovery, Security, Job Descriptions, IT Service Management, Change Control, Help Desk, Service Requests, SLAs - Service Level Agreements, and Metrics.
- www.ntcity.com - Technology Meeting Place
- www.cto-toolkits.com - This site is dedicated to supporting the goals of the Chief Technology Officer and includes links to tools and toolkits that meet those needs.
- blog.e-janco.com - Blog site
- www.disaster-recovery-planning-template.com
- www.disaster-planning-template.com
Specialized areas of Janco's practice include
- more info
- Electronic Books - Create network ready electronic books to eliminate paper. Improve accuracy, ease of use, and turnaround time. Reduce infrastructure costs and training.
- Outsourcing Reviews - Analyzing, planning, and managing the migration to services
- Information Systems Reporting - Developing and implementing methods to focus management's attention on critical data processing operational issues.
- Information Systems for Competitive Advantage - Assisting organizations in using computer systems and information delivery as tools to generate business and capture market share.
- Information Systems Planning and Development - Defining direction for the management of planning, developing, and implementing automated business systems that complement a firm's strategic needs.
- Internet and Intranet Web Site Design, Implementation and Management - Create Web sites for corporations and e-commerce.
- Data Network and Communication Planning - Developing architectures to support the use of decentralized data processing structures, including point-of-sale networks and multiple-site data entry and retrieval networks
- Competitive Compensation Analysis - Surveying the marketplace of compensation for data processing professionals, and assessing the alignment of compensation programs between competing organizations.
Recent Security Blog Postins
Top 10 Security Myths Security Myths Organizations are more secure now than they were a year ago The presence or absence of regulations greatly matters when it comes to...
20 Most Common Words Used in Phishing Attacks 20 Most Common Words Used in Phishing Attacks A new report from a cybersecurity company that analyzes how malicious files get past traditional defenses also...
FBI Begins Big Brother Security Implementation Lost of Privacy FBI begins Big Brother Security implementation In January of 2000 I wrote an article for PSR Reviews that forecast what was going to happen. The...
IT Security Decision Process IT Security Decision Process The IDG Enterprise Role & Influence of the Technology Decision-Maker survey helps CIOs understand their evolving roles and influence in todays...
Life cycle for business continuity and security breaches are the same When a security breach or business interruption occur, the life cycle from the start to the end are the same. First and foremost you must...
- more info