CIO, CTO, CSO, IT Service Management, IT Job Description, Sarbanes Oxley, and IT Salary News
CIO - CTO - CSO News
New Net Neutrality Rules Will Increase the Size of the FCC
The U.S. Federal Communications Commission (FCC) proposed new rules for net neutrality that will increase the federal bureaucracy and government oversight of the internet.
The FCC proposed new net neutrality rules that will allow broadband providers to charge companies like Netflix for preferential traffic management, according to a news report.
The FCC's proposal would prohibit broadband providers from slowing down or blocking traffic to specific websites, but allow them to give some traffic preferential treatment based on commercially reasonable terms. The FCC would determine what's commercially reasonably on a case-by-case basis.
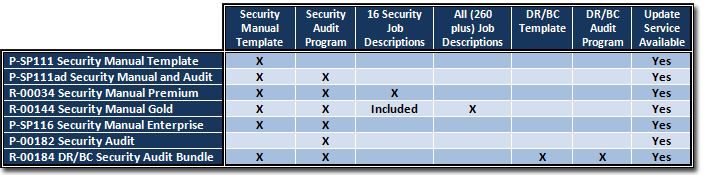
You can get all of Janco's templates in its IT Management Suite. When you do that you save over $2,500 and when implemented your enterprise is positioned to have a "WORLD CLASS" Information Technology function. You will be in compliance with all mandated requirements including all US and International requirements.
- more info
- IT Management Suite (CIO and CTO Special offer) - Save over $2,500
Hackers are attacking mobile devices
Primarily because mobile device applications have the potential to interact with confidential or sensitive information, many organizations see this area as a primary technology challenge to address and a main focus for security initiatives. Hackers have taken notice to this fact and have started targeting these mobile applications - which can ultimately lead to decreased trust in an application or an organization that uses it.
- more info
Mobility Policy Bundle (more info...) All of the policies below are included as individual MS Word files and a single PDF file. Electronic forms are all individual documents that are easily modifiable
- BYOD Policy Template (more info...) Includes electronic BYOD Access and Use Agreement Form
- Mobile Device Access and Use Policy (more info...)
- Record Management, Retention, and Destruction Policy (more info...)
- Social Networking Policy (more info...) Includes electronic form
- Telecommuting Policy (more info...) Includes 3 electronic forms to help to effectively manage work at home staff
- Travel and Off-Site Meeting Policy (more info...)
Workers apathy towards lost mobile devices is a major security risk
In a survey of U.S. workers in industries such as banking, retail, healthcare and energy there appears to be a general feeling of apathy toward mobile security.
Even if employees leak or lose corporate data, 25 percent of respondents say it's not their problem. Of those who actually lost a phone, 34 percent were not punished, 30 percent had to replace the device and 21 percent simply had a "talkin' to." Given such lackadaisical responses, it's no surprise that one-third of respondents who had lost their phones did not change their security habits afterwards.
Part of the problem is that employees don't really know what's at stake nor do they bother to understand the security portion of the user policy. In the survey, 59 percent estimated the value of the corporate data on their phones to be less than $500.
One out of four workers doesn't know company procedure for dealing with work device loss or theft, according to the survey. It's a communication problem that's not solely the worker's fault.
Additionally, CIOs say lots of employees will keep looking for a lost phone for weeks and not report it (although the policy says they should) out of fear it'll get wiped and they'll lose personal data. That's also perhaps a problem with the policy in relation to human behavior.
CIO IT Infrastructure Policy Bundle (All of the policies below are included as individual MS Word files and a single PDF file. Electronic forms are all individual documents that are easily modifiable)
more info
- Backup and Backup Retention Policy
- Blog and Personal Web Site Policy (Includes electronic Blog Compliance Agreement Form)
- BYOD Policy Template (Includes electronic BYOD Access and Use Agreement Form)
- Google Glass Policy
(Includes Google Glass Access and Use Agreement Form)
- Incident Communication Plan Policy (Updated to include social networks as a communication path)
- Internet, e-Mail, Social Networking, Mobile Device, Electronic Communications, and Record Retention Policy (Includes 5 electronic forms to aid in the quick deployment of this policy)
- Mobile Device Access and Use Policy
- Patch Management Policy
- Outsourcing Policy
- Physical and Virtual Server Security Policy
- Record Management, Retention, and Destruction Policy
- Sensitive Information Policy (HIPAA Compliant and includes electronic Sensitive Information Policy Compliance Agreement Form)
- Service Level Agreement (SLA) Policy Template with Metrics
- Social Networking Policy (includes electronic form)
- Telecommuting Policy (includes 3 electronic forms to help to effectively manage work at home staff)
- Text Messaging Sensitive and Confidential Information (includes electronic form)
- Travel and Off-Site Meeting Policy
- IT Infrastructure Electronic Forms
Disaster Recovery Digest
Disaster Recovery Digest
- more info
- Google data center security & disaster recovery This is a great video on physical security as well as the the software security. This is a great primer which all CIOs and Data...
- 10 best practices for cloud disaster recovery Cloud Disaster Recovery 10 Best Practices Creating out a complete cloud disaster recovery infrastructure can be cost prohibitive for many organizations. Ten best practices are:...
- Will your disaster recovery provider be in business when you need them? Disaster Recovery plans that depend on outsourcers face significant additional risk What if your were in Florida and the Hurricane season was in full swing...
- Options for a data center disaster recovery strategy Data Center disaster recovery strategy options A critical component of a disaster recovery business continuity is the data center disaster recovery strategy Hot...
- Infrastructure Key to Data Center Management and Disaster Recovery Infrastructure is key to data center management Data Center Management Issues Your data centers are stuck in a rut. While 90 per cent have...
Physical and digital security are the focus of CSOs
The migration of physical security technology to a network platform has made it easier and more convenient for the CSO and their organizations to integrate the various modalities of physical security into a unified configuration to better safeguard their employees, visitors, premises and material/intellectual property.
Open architecture further enables central control of the various security systems on a single platform, providing higher levels of operational efficiency across the enterprise as well as improved standardization of policies and procedures.
- more info
IT Trends that will impact business continuity
Six trends in IT will effect Disaster Recovery and Business Continuity.
- more info
- Security - Thanks to the NSA and GCHQ, (coupled with ongoing allegations against the Chinese), security, corporate privacy and encryption have moved swiftly up the corporate agenda. Identity management, which has often been seen as a nice to have, will become even more of a must have.
- Mobility and convergence - The rapid growth of mobility and the increase in numbers of mobile devices will carry on during 2014. This increase will go hand in hand with further growth in convergence, with all the associated threats and benefits.
- IPv6 - IPV6 will make an increasing impact in enterprise organizations, as infrastructure upgrades create greater corporate IPV6 awareness and increased connectivity to IPV6 customers and suppliers. IPV6 has a number of key mobility and roaming attributes, including the home address concept, which will raise some interesting challenges
- Big data - The rise in data volumes has changed the computing environment for many organizations, with challenges created in managing and reporting on the increasing amount of data, as well as dealing with the growing risk of data loss. 2014 will see data volumes continuing to grow, with a rise in sales of solutions which protect and manage these large amounts of data.
- Visibility reporting and remediation systems - With multiple threats, organizations have deployed multiple security solutions and lost sight of whats actually happening on the threat front. Consolidation to single suppliers will continue, but alongside that, deployment of reporting across multiple vendors will grow strongly.
- Cloud services - Growth in cloud systems and SaaS will continue, particularly for utility services and amongst early adopters. The two key challenges to growth include privacy concerns and security. Solutions that address these issues are beginning to increase at a faster rate than the market.
40 million credit and debit accounts breached
Target says that about 40 million credit and debit card accounts may have been affected by a data breach that occurred just as the holiday shopping season shifted into high gear.
The chain said that accounts of customers who made purchases by swiping their cards at terminals in its U.S. stores between Nov. 27 and Dec. 15 may have been exposed. The stolen data includes customer names, credit and debit card numbers, card expiration dates and the three-digit security codes located on the backs of cards. The data breach did not affect online purchases.
The breach affected all cards, including Target store brand cards and major card brands such as Visa and MasterCard.
The Minneapolis company said it immediately told authorities and financial institutions once it became aware of the breach and that it is teaming with a third-party forensics firm to investigate and prevent future breaches. It said it is putting all "appropriate resources" toward the issue.
Target Corp. advised customers to check their statements carefully.
- more info
Global compliance issues
The global regulation that has emerged since the financial crisis is the most rapidly evolving in nearly a century. This environment presents new challenges for compliance professionals as they navigate new regulations, implement new reporting processes within their organization, seek to create operational efficiencies and maintain an effective compliance program.
Chief Compliance Officers (CCO) and other industry professionals need to understand the regulatory reporting challenges faced by all types of enterprises, find lessons learned from others, as well as common practices that firms can leverage. Understanding these new regulations and their reporting requirements, as well as the complex data environment, are critical aspects of operating a strategic compliance program. Janco common practices for compliance excellence and share methods for new reporting implementation. Attendees will hear what challenges firms are facing, what technology and operational strategies they are using to adequately address emerging risks and how theyre ensuring adequate policies and procedures are in place.
- more info
IT spending slows
For the last 2 quarters Janco Associates (www.e-janco.com) has been saying that spending for IT in the U.S. is slowing. Now, it is reported in Computerworld that another research firm is saying the same thing. That research firm now projects that tech spending will increase by 3.9% this year; that's well below its earlier prediction of 5.7%.
The federal budget sequester, the government shutdown and the threat of default have had negative impacts on the economy and direct negative impacts on federal tech buying, as well as indirect impacts on CIOs who simply became cautious.
For instance, CIOs who might have bought servers to meet new demand for computing power are instead moving peak loads and special projects to infrastructure-as-a-service providers.
The White House estimates that the 16-day government shutdown reduced the growth rate of GDP in this quarter by 0.2% to 0.6%.
Next year, that firm projects that U.S. business and government purchases of IT goods and services will rise by 5.3%, thanks to a revived housing market, modest improvement in employment and consumer spending, and improved exports. In contrast Janco Associates feels that spending will be less until after the election next year.
- more info
Persons with disabilities at higher risk during a disaster
UN survey shows needs of persons with disabilities largely ignored during disasters
A high proportion of persons with disabilities die or suffer injuries during disasters because they are rarely consulted about their needs and Governments lack adequate measures to address them, according to a United Nations survey released ahead of the International Day for Disaster Reduction.
The online survey, produced by the UN Office for Disaster Risk Reduction (UNISDR) and partners, consulted nearly 6,000 persons with disabilities in 126 countries on how they cope and prepare for disasters.
The results show that people living with disabilities across the world are rarely consulted about their needs in times of disasters. In cases where they need to evacuate such as during floods or earthquakes, only 20 percent of respondents said they could evacuate immediately without difficulty, 6 percent said they would not be able to evacuate at all and the remainder said they would be able to evacuate with a degree of difficulty.
- more info
CIO Toolkits
Tool Kits -- CIO CTO Tools
Disaster Planning
IT-ToolKits.com is the resource site for
Information Technology management. This site contains the Information Technology and management infrastructure tools that the CIO, CSO, and CFO can use for Sarbanes Oxley, Disaster Recovery, Security, Job
Descriptions, IT Service Management, Change Control, Help Desk, Service Requests, SLAs - Service Level Agreements, and Metrics. Site includes Browser and Operating System Market Share White Paper and IT Salary Survey Data.
Disaster Recovery Templates are Sarbanes Oxley compliant and the Disaster Recovery Template is included in the Sarbanes Oxley Compliance Kit
IT-Toolkits.com supports a wide range of industries and enterprises of all sizes. Our clients include over 2,500 premier corporations from around the world, including over 250 of the Fortune 500.
- more info
Business interruptions to consider when creating a bcp
Business interruptions vary widely in more than duration. As you design your plan, consider the probability of threats that are:
Historical - events that have occurred (Power outages, earthquakes, hurricanes)
- Human - events likely from carelessness, malicious intent, fatigue, or lack of training
- Geographical - events likely as a result of the location of your business (floods, storms, lightning strikes, earthquakes, typhoons, tsunamis)
- Localized - events due to system malfunctions (assembly line failures, computer crashes, sprinkler activations, chemical spills)
- Planned - scheduled events (software upgrades, system tests) that go awry
Follow us at https://twitter.com/@itmanagercio
- more info
Security will become more complex with the evolution of the Internet of things
Recent revelations on the extent of data capture by the US goverment and companies in genreral raise interesting security questions for CIOs and the public in general
The Internet of Things is a network of Internet-enabled, real-world objects, such as nanotechnology, consumer electronics, home appliances, sensors of all kinds, embedded systems, and personal mobile devices. It includes enabling network and communication technologies, such as IPv6, web services, RFID, and 4G networks. Today this is a reality seeing the people are using mobile devices. For example, you can monitor your home security, lights, heating, and cooling from your smartphone. You can purchase a refrigerator that monitors its processes and sends reports to your smartphone.
Janco predicts that, by 2020, possibly 50 billion devices will be connected, a number that is 10 times that of all current Internet hosts, including connected mobile phones3. This amazing number of connected devices, along with the required
conditions for maintenance and effective operation, present intricate and complex challenges that affect Internet-of-Things
adoption and growth.Recent Articles:
- more info
- Risk Assessment Methodology Risk Assessment Methodology Risk Assessment Methodology extracted from Jancos Security Manual Template Risk management is a process to identify, assess, manage and control potential events...
- Google data center security & disaster recovery This is a great video on physical security as well as the the software security. This is a great primer which all CIOs and Data...
- CIOs are not conducting cloud computing risk assessments CIOs are not conducting cloud computing risk assessments A new survey by Protiviti has found that cyber security tops chief information officers concerns, with 84...
- Security Audit a Necessary Part of Compliance Security Audit and Compliance Why do we need to do a security audit is question that many IT pros ask. Many organizations have to respond...
- 10 BYOD Best Practices for CIOs BYOD Best Practices for CIOs Bring Your Own Devices (BYOD) is exploding all over corporations. CIOs are in the cross hairs and need to follow...
IT Hiring News Digest
IT Hring News - Digest of Recent Articles
- IT Job Market Improving? Some say the IT Job Market is improving from the 2009 slump IT Job Market Improving? An on-line job portal, Dice says IT degree graduates...
- Poor job picture impacts IT hiring prospects IT hiring trends have been driven by overall job market conditions IT hiring prospects do not look good. According to the BLS from June 2012...
- IT Job Market grows 10 major findings Where are the jobs for our college graduates? IT Job Market growth is slow. Over the last few years the number of new jobs for...
- CIO confidence wanes Hiring slows CIO worries IT job market growth continues to slow from 9,800 jobs in January and 5,500 jobs in February to 5,400 in March ...
- IT hiring CIOs have mixed feelings on Fourteen percent of U.S. chief information officers (CIOs) surveyed recently plan to expand their IT teams in the second quarter of 2013, according to a...
IT Job Descriptions
- more info
Salary Data
Unmanaged administrarive right pose a security and compliance risk
Unmanaged administrator rights pose a critical security challenge, making possible malware attacks that exploit elevated privileges and encouraging employees to run unauthorised applications that generate inadvertent, unquantifiable risk.
Privilege management is a practical solution to the problem of the loosely-managed desktop. The following is an outline of the key business, technical and implementation considerations when assessing an investment in such technology.
- more info
- Security: the permissive elevation of admin privileges is an obvious security risk. Users can potentially run unauthorised software or even malware. Malware attacks routinely ask for such privileges so these represent a significant security vulnerability.
- Compliance: policing admin rights has become a regulatory issue not only to meet legal requirements imposed in some countries but to satisfy independent audits. The global nature of financial services means that the toughest regulation is always the one to worry about.
- Efficiency and cost: there is a potential to reduce helpdesk workload. Low-level functions (e.g. power management, connecting to local printers) can be granted without staff involvement, based on policies. These policies will also regulate all application elevation, again lowering the authorization overhead.
Employees are key to security compliance
The best safe in the world is worthless if you don't keep the combination a secret. The same concept holds true for data protection. No matter how state-of-the-art your encryption technology is, if your employees aren't security-savvy, it's not guaranteed to be effective.
Security incidents are rising at an alarming rate every year. As the complexity of the threats increases, so do the security measures required to protect networks and critical enterprise data. CIOs, Data center operators, network administrators, and other IT professionals need to comprehend the basics of security in order to safely deploy and manage data and networks.
Securing a typical business network and IT infrastructure demands an end-to-end approach with a firm grasp of vulnerabilities and associated protective measures. While such knowledge cannot stop all attempts at network incursion or system attack, it can empower IT professionals to eliminate general problems, greatly reduce potential damages, and quickly detect breaches.
Related Articles
- more info
- Life cycle for business continuity and security breaches are the same When a security breach or business interruption occur, the life cycle from the start to the end are the same. First and foremost you must...
- Employees drive the movement to BYOD and cloud computing CIOs face a security nightmare with the drive towards BYOD and cloud computing High achieving employees typically want newer,faster and higher performance hardware than their...
- 10 steps to jump start your business continuity planning business continuity planning 10 steps to jump start your BCP Business Continuity For many businesses there is some technology component that allows them...
- Security Ethics Collide Security Ethics are a growing concern for many According to a new report by Symantec CIOs need to be concerned about security and ethics, half...
- Many CIOs have not addressed cloud security issues Less than 50% of all organizations have policies in place that for vetting cloud computing applications for possible security risks before deploying them. The number...
Workforce mobility a productivity issue for CIOs
Part of the CIO's job is to support maximum productivity by choosing appropriate infrastructure for laptops and other devices to meet the individualized needs of
mobile employees. But IT leaders also must support the mobile infrastructure in a way that is designed to minimize costs, simplify administration efforts, protect against mobile-specific threats, and ensure security. Key enablers of the mobile workforce include the following:
- more info
- Outstanding security and network accessibility
- Simple, intuitive systems and data management tools
- A streamlined process for backing up critical data
- Smooth transitions when changing hardware or software
Articles on the Chief Mobility Officer - CMoO
Articles on the Chief Mobility Officer - CMoO
- more info
- Is a Chief Mobility Officer necessary Chief Mobility Officer now almost a necessity The idea of a company having a chief mobility officer (CMO) is not a new one. But as...
- 10 reasons why organizations need a Chief Mobility Officer (CMoO) Chief Mobility Officer (CMoO) business case Here are ten reasons your company needs a chief mobility officer: To deliver mobility solutions for the enterprise to...
- Compliance Program 10 Steps 10 Steps to a World Class Compliance Program A Compliance program, or a lack of one, is now putting CIOs and CSOs under a great...
- Released Internet and Information Technology Position Descriptions HandiGuide, 2013 Edition Internet and Information Technology Position Descriptions HandiGuide, 2013 Edition Janco has released the Internet and IT Position Descriptions HandiGuide® which is over 700 pages; includes...
- Top 10 CIO Productivity and Budgeting Issues CIO Productivity Kit The best companies, and their CIOs, recognize the importance of ready access to the right information to drive the right choices...
CIO and IT Manager Management News
CIO and IT Manager Management News
- more info
- Unmanaged administrarive right pose a security and compliance risk
- Almost 80% have DR plans in place - But
- Data breaches can be stopped
- Business Continuity Planning and Survival
- Disaster Recovery Business Continuity Testing Options
- Cybercrime is on the rise
- Disaster Recovery is for more than major events
- Business Record Management is Difficult at Best for Many CIOs
- Data breaches impact more uses in 2011 according to analysis of data
- Disaster Recovery for mid-sized businesses
- Business interruptions to consider when creating a bcp
- Social Networking Policy
- Disaster Planning budget discussion
- Disaster planning state of the art solutions
- BYOD improves productivity
- Mobile devices put a strain on help desk staff
- Meeting productivity improvement
- Labor Force Participation Rate at Lowest Level in over 40 Years
- Mobile device usage improves productivity
- EU Proposes New Security Requirements
- Proposed new manadated compliance for executive and CIO compensation
- Security breaches can go un-detected for a lomg time
- Cybersecurity now a CEO concern
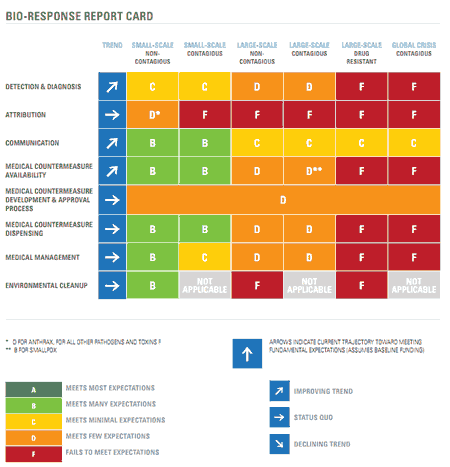
Influenza A(H7N9) virus
The World Health Organization has published a risk assessment of the Influenza A(H7N9) virus which has killed a number of people in China.
- more info