Security Policies Out of Control
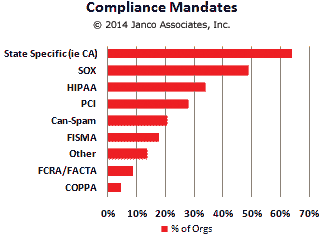
More small and mid-sized business are impacted by state mandated (i.e. California, Massachusetts, New York, and others) than federal and SEC mandates.
CIOs and CSOs are now under a great deal of pressure, not only from their executive management, but also from a range of governmental and industry regulatory bodies to meet new requirements. Failure is not an option.
Janco has created a ten step program that helps them address compliance issues directly. The program, when used in concert with Janco's Compliance Management products gets them in front of the the issue.
The ten step program Janco recommends is:
- Implement a Security Officer Position
- Conduct a compliance risk assessment
- Document
- Know the operating environment
- Prepare for Incidents
- Expect the worst to happen
- Control media and electronic files
- Train users
- Log and audit
- Clean up old data and system.
Security Policies and Procedures
Today, more than ever, companies are confronted with a broad array of electronic document issues, including data retention policies and e-discovery during litigation. Failing to comply with rules regarding such electronic data can cost millions of dollars.
 Every corporation and organization needs a universal and comprehensive set of security processes to safeguard the use of their computers, all related equipment and information assets which support enterprise wide operations. The Security Manual Template meets those needs.
Every corporation and organization needs a universal and comprehensive set of security processes to safeguard the use of their computers, all related equipment and information assets which support enterprise wide operations. The Security Manual Template meets those needs.
For instance in one case, the SEC alleged that a company failed to produce tens of thousands of emails sought by the SEC in two investigations. The court entered an 8-page consent judgment against the company.
Whether it is government agencies, research facilities, banking institutions, credit card processing companies, hospitals or your company's computers - the risk of compromising private information is very high -- especially when when conducting a disaster recovery tests. Since business relies so heavily on technology today, business risk becomes technology dependent. The possibility of litigation is part of business. It has always been a risk of doing business, but because technology and today's business are so intertwined, business risk has a higher threat level.
The Security template complies with Sarbanes-Oxley, HIPAA, Cobit and mandated state requirements. The template includes a sensitive information policy and has been updates to include checklists for employee terminations and other security related forms. In the age of information, organizations live and die on one thing, information. "Security breaches can have dramatic impact the information assets of every organization", stated Janco's CEO.
Implementing an understandable and usable set of security policies and procedures is a necessity. Janco's Security Manual Template provides guidelines and actual policies and procedures for any organizations. It is a model any sized organization can use. It is comprehensive without being wordy or pedantic.
This electronic document is over 230 pages and can be used in the creation of security policies and procedures for any size entity. The process of creating effective policies and procedures that comply with mandated requirements such as Sarbanes-Oxley and Massachusetts Data Protection with the current security threats and tight budgets is daunting.