CIO, CTO, CSO, IT Service Management, IT Job Description, Sarbanes Oxley, and IT Salary News
CIO - CTO - CSO News
Intellectual property theft is a major security risk that all companies face
For many companies, in particular in industries like pharmaceuticals, software development, or entertainment, their intellectual property is more valuable than any physical asset. And with the increasing need to collaborate with external business partners to accelerate product life cycles and enhance innovation, there is a greater risk for sensitive information to be compromised.
With identify theft and cyber attacks on the rise, you're facing new pressures to protect sensitive information. In fact, in 46 states have now passed data security laws that apply to companies that do business with residents of those states. These laws are designed to protect residents against identity theft by mandating security practices
such as:- more info
- Implementing an information security program
- Encrypting data
- Notifying customers in the event of a security breach that compromises unencrypted personal information
One step to improve security on Windows based PCs
If you take Windows XP out of the mix -- when Microsoft support for the archaic OS expires -- there will likely be far fewer security bulletins rated as Critical, and the idea of putting systems at risk by running with unobstructed administrator privileges will be mostly be a thing of the past.
Regardless of which version of Windows you use, though, the Avecto report underscores a very simple reality. An attacker can typically only execute malicious code in the context of the currently logged in user, and if that user is a standard user without access to critical system functions, and with no ability to run unknown software without explicit administrator permission, most threats would be rendered harmless.
- more info
New job title - Chief Digital Officer - CDO
The job of chief digital officer (CDO) has recently emerged as a new role on the leadership team, as organizations are looking to bring in digital capabilities and seeing the need for an executive with a new set of competencies that combines strategy, marketing, and technology. Many are considering hiring or have already hired a digital leader to oversee enterprisewide digital strategy.
263 IT Job Descriptions and Organization Charts
The Internet and IT Position Descriptions HandiGuide® was completed in 2014 and is over 700 pages; which includes sample organization charts, a job progression matrix, and 263 Internet and IT job descriptions. The book also addresses Fair Labor Standards, the ADA, and is in a new easier to read format.
- more info
Security Tip - Always Check Credentials
Always Check Credentials. The receptionist's PC had been running slowly, so he was pleased when a woman arrived and announced that she was a technician. She dropped the name of the IT manager and said, "Don't bother logging off, I'll only be a few minutes." Ten minutes later she was gone - along with a bunch of confidential documents.
Those documents enabled an unscrupulous competitor to beat the company to a lucrative contract. If the receptionist had checked the technician's credentials with the IT Manager, the security breach could have been avoided. Not only did the receptionist learn a lesson; the company also learned that they should control access to sensitive information!
- more info
10 Backup Best Practices supplementing a disaster recovery and business continuity solution with the cloud
10 Backup Best Practices supplementing a disaster recovery and business continuity solution with the cloud
10 Backup best practices - supplementing a disaster recovery and business continuity back-up solution with the cloud Backup best practices are used by many CIOs who want to improve their ability to recover from system failures and data loss. This Continue reading
- more info
- Disaster Recovery Business Continuity Template
- Disaster Recovery Business Continuity Audit Program
- Disaster Recovery Remote Sites
- Disaster Recovery Business Continuity Template and Security Manual Template Bundle
- Disaster Recovery Business Continuity Template and Security Manual Template Audit Bundle
- Disaster Recovery Business Continuity Template and Safety Program Bundle
- Disaster Recovery Business Continuity Template, Security Manual Template, and Safety Program Bundle
- Disaster Recovery Electronic Forms
- BIA - Business Impact Analysis Methodology
- Compliance with ISO Standards
- Compliance with ISO 22301 - Business Continuity Management (BCM)
- Compliance with HIPAA Standards
- Enterprise and Worldwide License Options
Change the combination on opened laptop locks
- more info
When laptops have cables with combination locks for securing their devices at their workstation, they always remember to turn the tumblers when they secure the laptop. But what happens when they unsecure the laptop? Many people won't turn the tumblers on the opened lock because it is much easier to lock the laptop later if the combination is already set. About half a dozen laptops in our office disappeared one day. The laptops were stolen by someone who came by when the laptops were not there and noted the combination. They came back later when the laptops were there and used the combination they had noted earlier.
Cyber-Attack Digest
Cyber-Attack Digest - recent articles:
- more info
- Anatomy of a Chinese Cyber Attack Cyber Attack How the Chinese do it A Chinese cyber Attack (a Stuxnet-style attack) frequently makes its first entry into a companys secure network...
- Cyber attacks are on the rise Cyber attacks are more extensive as the criminal element moves in Cyber attacks and threats to networks and enterprise data are not going away. Risk...
- Security cyber war recent articles Cyber war continues Cyber war and security recent postings: CIOs worry more about cyber threats with mobile computing Cyber threats are now a much greater...
- CIOs worry more about cyber threats with mobile computing Cyber threats are now a much greater concern with the expansion of the use of mobile devices and services. At the same time online criminals...
- Life cycle for business continuity and security breaches are the same When a security breach or business interruption occur, the life cycle from the start to the end are the same. First and foremost you must...
Infrastructure and Other Top CIO concerns
As profitability is more difficult to find than prior to the financial crisis, 2014 will be a year of foundational investment for the financial markets, with the primary focus on investment in IT infrastructure, according to new research from Ovum.
This investment is required for finding new opportunities to drive profit, by moving into new markets, trading venues, geographies and asset classes. Over two thirds of respondents queried on infrastructure spending forecasted an increase of between one and six percent in their outlay.
Meanwhile, the ongoing volatility in global markets is making profitability a challenge and, as a result, customer loyalty is declining. As neither the buy side nor the sell side can guarantee profit margins in current market conditions, both sides are set to invest in IT systems that improve service levels in the hope that it positively impacts customer satisfaction and ultimately customer loyalty.- more info
"Financial markets will face two main challenges in 2014, with the difficulties of achieving profits in a post-financial crisis environment and complying with the ever-increasing raft of rules and regulations," says a senior analyst, financial services technology at Ovum. "This will drive an increase in IT infrastructure spending, as well as a focus on servicing systems to improve customer loyalty levels.
'Regulatory compliance will continue to be a particularly large area of spending. The ever-increasing range of rules and regulations is requiring large investments and is currently consuming as much as 40% of overall IT budgets across the financial markets.'
CIOs are paid to lead
A CIO is paid to lead. But it's difficult to do so when you don't have the right organizational structure in place. A house, after all, is only as strong as its foundation. So whether you're "the new guy" as a CIO or you've worked within your current position for a year or longer, you should carefully consider the following nine winning organizational moves to implement for your IT department. As compiled by Janco Associates, the best practices here aren't the stuff of rocket science (even if you happen to supervise a number of rocket scientists). Instead, they're a useful collection of suggestions that cover both the big picture, such as alignment with company-wide strategies, and the day-to-day, like assigning key roles to your employees. By putting the following in play, you'll find that you've covered many critical bases, including the need to delegate, develop talent, ensure business continuity, track tech trends and monitor the competition. Better yet: It's not an "all or nothing" list. You can adapt only one or two ideas and still take advantage of results. For more about Janco's list, click here. - See more at: http://www.cioinsight.com/it-management/leadership/slideshows/nine-ways-to-better-organize-your-it-department-08/#sthash.G89cO1jc.dpufA CIO is paid to lead. But it's difficult to do so when you don't have the right organizational structure in place. A house, after all, is only as strong as its foundation. So whether you're "the new guy" as a CIO or you've worked within your current position for a year or longer, you should carefully consider the following nine winning organizational moves to implement for your IT department. As compiled by Janco Associates, the best practices here aren't the stuff of rocket science (even if you happen to supervise a number of rocket scientists). Instead, they're a useful collection of suggestions that cover both the big picture, such as alignment with company-wide strategies, and the day-to-day, like assigning key roles to your employees. By putting the following in play, you'll find that you've covered many critical bases, including the need to delegate, develop talent, ensure business continuity, track tech trends and monitor the competition. Better yet: It's not an "all or nothing" list. You can adapt only one or two ideas and still take advantage of results. For more about Janco's list, click here. - See more at: http://www.cioinsight.com/it-management/leadership/slideshows/nine-ways-to-better-organize-your-it-department-08/#sthash.G89cO1jc.dpufA CIO is paid to lead. But it's difficult to do so when you don't have the right organizational structure in place. A house, after all, is only as strong as its foundation. So whether you're "the new guy" as a CIO or you've worked within your current position for a year or longer, you should carefully consider the following nine winning organizational moves to implement for your IT department. As compiled by Janco Associates, the best practices here aren't the stuff of rocket science (even if you happen to supervise a number of rocket scientists). Instead, they're a useful collection of suggestions that cover both the big picture, such as alignment with company-wide strategies, and the day-to-day, like assigning key roles to your employees. By putting the following in play, you'll find that you've covered many critical bases, including the need to delegate, develop talent, ensure business continuity, track tech trends and monitor the competition. Better yet: It's not an "all or nothing" list. You can adapt only one or two ideas and still take advantage of results. For more about Janco's list, click here. - See more at: http://www.cioinsight.com/it-management/leadership/slideshows/nine-ways-to-better-organize-your-it-department-09/#sthash.lWy9izzG.dpufA CIO is paid to lead. But it's difficult to do so when you don't have the right organizational structure in place. A house, after all, is only as strong as its foundation. So whether you're "the new guy" as a CIO or you've worked within your current position for a year or longer, you should carefully consider the following nine winning organizational moves to implement for your IT department. As compiled by Janco Associates, the best practices here aren't the stuff of rocket science (even if you happen to supervise a number of rocket scientists). Instead, they're a useful collection of suggestions that cover both the big picture, such as alignment with company-wide strategies, and the day-to-day, like assigning key roles to your employees. By putting the following in play, you'll find that you've covered many critical bases, including the need to delegate, develop talent, ensure business continuity, track tech trends and monitor the competition. Better yet: It's not an "all or nothing" list. You can adapt only one or two ideas and still take advantage of results. For more about Janco's list, click here. - See more at: http://www.cioinsight.com/it-management/leadership/slideshows/nine-ways-to-better-organize-your-it-department-09/#sthash.pF2ECXTa.dpufA CIO is paid to lead. But it's difficult to do so when you don't have the right organizational structure in place. A house, after all, is only as strong as its foundation. So whether you're "the new guy" as a CIO or you've worked within your current position for a year or longer, you should carefully consider the following nine winning organizational moves to implement for your IT department.
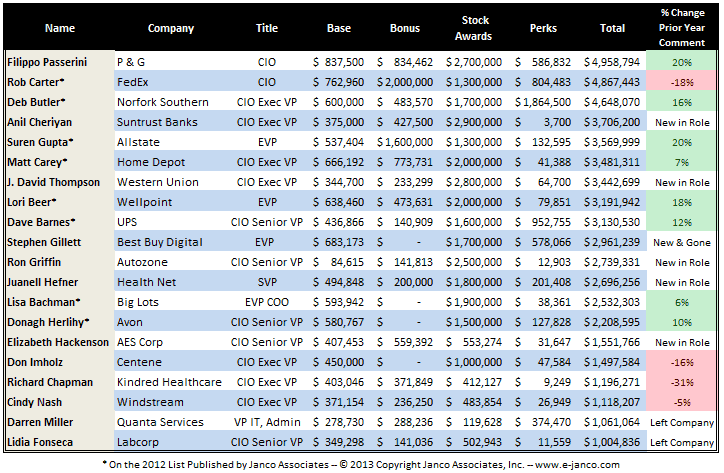
Highest Paid CIOs in publicly traded companies in 2012 as reported to the SEC in 2013
As compiled by Janco Associates (www.e-janco.com), the best practices here aren't the stuff of rocket science (even if you happen to supervise a number of rocket scientists). Instead, they're a useful collection of suggestions that cover both the big picture, such as alignment with company-wide strategies, and the day-to-day, like assigning key roles to your employees. By putting the following in play, you'll find that you've covered many critical bases, including the need to delegate, develop talent, ensure business continuity, track tech trends and monitor the competition. Better yet: It's not an "all or nothing" list. You can adapt only one or two ideas and still take advantage of results.
- more info
Ethics in the business world is a complex issue
What is right vs. wrong is pretty obvious. If it is not obvious, you have more work to do that can be shared here. The real tough decisions now are when two values that you deeply believe in are in conflict with each other. Now what do you do? How do you do it? And what tools, techniques, different training do you need to handle these tough decision.
For example: Truth vs. loyalty. How do you handle a situation when you want the truth and the person is loyal to someone or something else? What insights, techniques are available to help discern the process to make the best decision?
Or how about justice vs. mercy, what is your criteria for justice, mercy? Justice according to what, the law, code of ethics, values statement, mission statement or?? Mercy, based on what? How transparent are you as to which one you chose? If youre not transparent, why not?What is crucial here is that one needs to truly know what values one believes and has internalized BEFORE a situation occurs, so that there is no hesitation about what needs to do done, when it needs to be done and why it needs to be done.
IT Job Descriptions
- more info
Salary Data
New Technology - 3D Printers
3D printers apply materials such as plastic and metal in fine layers to create objects ranging from buttons and small widgets all the way up to walls for prefabricated homes.
Although 3D printers have been in use for more than 20 years, the market has soared in the last few years as companies buy the devices to make prototypes of planned new products, and to quickly launch full-scale production.
Recently, home 3D printers selling for less than $1,000 have let consumers make replacement parts for appliances, toys, decoration and other items at home. The market is expected to see strong long-term growth.
- more info
Business continuity after a disaster depends on communication
When a CEO thinks Business Continuity, he thinks of the safeguards that should be in place ensuring business operations are not disrupted. However, due to the heavy dependency on Information Technology, a business leaders first priority is to have adequate data backups in order to enable recovery in case of a disaster or any loss of data, and to ensure that systems remain available 24x7.
The right way to evaluate the quality of your system and data protection is to evaluate the Recovery Time Objective (RTO) and Recovery Point Objective (RPO). These metrics define how long you think it will take you to get back online and how current the data has to be.
All Business Continuity Disaster Recovery Planning efforts need to encompass how employees will communicate, where they will go and how they will keep doing their jobs. The details can vary greatly, depending on the size and scope of a company and the way it does business. For some businesses, issues such as supply chain logistics are most crucial and are the focus on the plan. For others, information technology may play a more pivotal role, and the Business Continuity Disaster Recovery Plan may have more of a focus on systems recovery.
- more info
CIOs need to be ready for the next wave of new technology
- more info
The next wave of business technology innovation is happening right now. The technologies themselves -- cloud computing, mobile devices, social media, data analytics -- aren't new. What is rapidly changing is their increasing maturity and adoption in business today and the demonstrable impact they are having to either drive innovation in one's business model or cause competitive disruption while yielding margin improvement.
In some cases, these technologies allow you to minimize your dependency on the IT organization to get things done. In fact, demand for these technologies is often coming from the business itself -- from your workforce -- over the concerns and fears of IT. This is presenting a whole new set of challenges in managing IT across the enterprise.
Disaster Recovery Plan Template
An information technology (IT) disaster recovery (DR) plan provides a structured approach for responding to unplanned incidents that threaten an IT infrastructure, which includes hardware, software, networks, processes and people. Protecting your firm's investment in its technology infrastructure, and protecting your firm's ability to conduct business are the key reasons for implementing an IT disaster recovery plan. SearchDisasterRecovery.com's free downloadable IT disaster recovery template will help facilitate the initiation and completion of an IT DR plan.
In this guide, you will learn everything you need to know about putting together an IT disaster recovery plan. You'll learn step-by-step IT DR plan development and the most important IT disaster recovery planning considerations. Use our IT disaster recovery plan template, which can be printed out and customized for your company's unique needs.
- more info
Blocking IP Theft
Security Manual - Comprehensive, Detailed, and Customizable
Organizations need to take the following steps to block IP theft:
- more info
- Organisations should have a policy, backed by enforcement, covering the use and protection of IP in all formats, physical or digital. The policy should cover organisational and non-organisational IP and how staff can use, share and protect it weaving in both IT and information security aspects. Staff, especially those dealing with IP, should be
- Organisations should implement a process to identify and manage the information risks that arise from sharing information with its upstream suppliers and downstream customers and set its assurance requirements accordingly. Contracts with new suppliers should include IP clauses and existing contracts renegotiated to enhance IP protection.
- To protect digital IP, in addition to fundamental controls such as access management, hardening servers and secure system development (as described in the ISF Standard of Good Practice), deploying technologies such as digital rights management, content filtering and logging, along with a data analytics solution (to spot unusual activity) should be considered, as should the provision of a forensics capability (in house or external) to collect evidence should IP theft be attempted or occur.
Security Articles
Security Topics
- more info
Disaster Recovery Current Articles
Current Disaster Recovery Articles

- more info
- The new business continuity and disaster recovery standard ISO 22312 versus ISO 22301 New business continuity and disaster recovery standard CIOs, Business continuity practitioners, vendors and consultants have ISO 22313 (see https://www.e-janco.com/DRP.htm) as a handy tool that addresses...
- Finding Disaster Recovery Tools Adobe falls short Adobe is not a good source for Disaster Recovery tool development Janco has just updated it Threat Vulnerability Assessment tool as it updates it Disaster...
- Business Continuity Planning for Survival Under Stress Business continuity and disaster recovery planning took a real hit in the recession that started in 2008. First many companies reduced the number and intensity...
- Life cycle for business continuity and security breaches are the same When a security breach or business interruption occur, the life cycle from the start to the end are the same. First and foremost you must...
- 10 Commandments of Disaster Recovery and Business Continuity 10 commandments of disaster recovery and business continuity planning As requirements for avoiding downtime become increasingly stringent, administrators need tools and platforms that can help...
Reused passwords can be an issue
A breach that potentially leaked the user names and passwords of LivingSocial's more than 70 million users could seriously impact the subscribers, if they reused their passwords on other sites.
On April 27, the deal-finding service alerted its users that criminals had breached the company's security and taken some customers' user names and passwords, as well as names, email addresses and dates of birth for some users. The passwords were stored as hashed values, although using SHA-1, a weaker hashing algorithm.
LivingSocial forced every user to change their password, but previous data breaches have shown that a majority of people reuse passwords across sites, threatening their accounts on other Web services and even their employer's network.
It's important to consider the possibility that some of your employees may have used the same password on LivingSocial that they use to access their work email and VPN accounts.
- more info
Mobile targeted threats is putting organizations at risk of cyber-espionage
Lacoon Mobile Security has warned that Mobile Remote Access Trojan (mRATs) infections of smartphones is increasing and bypassing encryption and sandboxes solutions. This statement is made based on the results of its research that discovered one in 1,000 smartphones has mRAT spyware installed. Conducted in partnership with global mobile network providers, the study sampled 2 million subscribers in late October 2012. It found that of 52 percent of infected devices were attributed to iOS and 35 percent to Android-based mobile devices.
The study showed how the mRATs were capable of intercepting 3rd party applications, such as WhatsApp, despite their guarantee of encrypted communications. The worrying element of this trend is that, with enterprises rapidly adopting mobile device management solutions, mRATs can bypass their security controls in the same manner.
- more info
Over 30% of all enterprise data resides remotely
Remote or branch offices are increasingly at the front lines of business - they have the closest contact with customers and business partners and therefore can have a dramatic impact on the success of the business. Analysts estimate that there are more than four million remote offices in the United States alone.
Many of these offices run autonomously from headquarters andare responsible for managing their own operations - including protecting and retaining the electronic information that they generate. Ignoring the recovery needs of this remotely storeddata is simply not an option. As companies expand operations into new markets, the percent-age of total corporate data in remote offices is increasing - the industry average is now 31%. However, many companies may not be adequately protecting these assets to ensure fast, reli-able recoverability.- more info