"Order Cloud Outsourcing Template Sample Cloud Outsourcing Contract" http://bit.ly/1dQPqzs #outsourcing
CIO, CTO, CSO, IT Service Management, IT Job Description, Sarbanes Oxley, and IT Salary News
CIO - CTO - CSO News
What tools do the feds have to fight cypercrime?
Testifying before a Congressional hearing entitled: "Protecting Consumer Information: Can Data Breaches Be Prevented?" US Secret Service Criminal Investigative Division Deputy Special Agent in Charge said: "While there is no single solution to prevent data breaches of U.S. customer information, legislative action could help to improve the Nation's cybersecurity, reduce regulatory costs on U.S. companies, and strengthen law enforcement's ability to conduct effective investigations."
One of the most poorly understood facts regarding data breaches is that it is rarely the victim company that first discovers the criminal's unauthorized access to their network; rather it is law enforcement, financial institutions, or other third parties that identify and notify the likely victim company of the data breach by identifying the common point of origin of the sensitive data being trafficked in cyber crime marketplaces.
The Secret Service has as one of its primary roles to protect the US financial system, is now leading the investigation into the Target and Neiman Marcus breaches. It is in fact the Secret Service who alerted Target to the problem. The New York Times wrote: Target had no clue until the Secret Service alerted the company about two weeks before Christmas. Investigators who had been tracking these criminals overseas and monitoring suspicious credit activity spotted in December one common thread: charges and payments made at Target.
While he didn't detail the exact systems the agency uses during the hearing, the Secret Service said "proactively investigates cyber crime using a variety of investigative means to infiltrate these transnational cyber criminal groups."
- more info
Getting BYOD Management Under Control
As employees bring their own personal devices to work, they are demanding access to corporate data in real time. IT must respond to BYOD, balancing productivity gains with security and user privacy. A recent IDG Research survey found many IT professionals saw advantages in cloud-based Mobile Workspace Management (MWM) technology.
BYOD include consumer SmartPhones and tablets which are making their way into your organization. Going mobile makes employees happier and more productive, but its also risky. How can you say yes to a BYOD choice and still safeguard your corporate data, shield your network from mobile threats, and maintain policy compliance?
With the advent of Bring-Your-Own-Device - BYOD and the ever increasing mandated requirements for record retention and security CIOs are challenged to manage in a complex and changing environment.
- more info
2014 starts with a security beach
Phone numbers paired with user names of over 4.6 million alleged Snapchat users were posted online by hackers, a few days after a security research group claimed a vulnerability in the social sharing service that could allow attackers to match phone numbers to Snapchat accounts.
"This database contains username and phone number pairs of a vast majority of the Snapchat users," said a post on website SnapchatDB.info. The account has since been suspended, apparently by the hosting service.
Many organizations fail to realize the benefits of security information management due to the often exhaustive financial and human resource costs of implementing and maintaining the software. However, Janco's Security Manual Template - the industry standard - provides the infrastructure tools to manage security, make smarter security decisions and respond faster to security incidents and compliance requests within days of implementation. The template provides a framework for evaluating SIM services and shows how they could be applied within your organization.
- more info
CIO concerns digest - top 5 current articles
Top 5 current articles on CIO concerns:
- more info
- Budgeting Puts Fear Into Many CIOs and IT Managers Budgeting for 2014 is challenge for many CIOs Budgeting can be a harrowing experience or an opportunity to show that you are an executive who...
- Data Center Trends for 2014 Budgets for 2014 reveal Data Center Trends New technologies and applications are impacting the data center management processes. This includes cloud computing, social media, mobile...
- Top 10 Things a CIO Needs to Add Value Top 10 for CIOs -What does the CIO have to do to be viewed as a business person versus a technologist? There are many strategies...
- CIO Issues with workload, budgeting, and staffing CIO issues are made more complex as staffing levels and budgets remain flat As the 2014 budgeting cycle starts, CIOs clearly have their hands full...
- Top 10 CIO Productivity and Budgeting Issues CIO Productivity Kit The best companies, and their CIOs, recognize the importance of ready access to the right information to drive the right choices...
Will Smartphones and Tablets become the cameras of 1984?
The sophistication of our mobile devices has grown in the last decade - but they are set to predict our next move, purchase and action in the future.
Within 5 years smartphones and tablets will utilize cognizant computing - the next step in personal cloud computing - rendering them capable of predicting our next move based on what it knows.
Smartphones are becoming smarter, and will be smarter than you by 2017according to some researchers. For example, if there is heavy traffic, it could wake you up early for a meeting with your boss, or simply send an apology if it is a meeting with your colleague. The smartphone will gather contextual information from its calendar, its sensors, the user's location and personal data.
By adding an array of features to mobile devices including GPS trackers, cameras, apps and sensors that can improve and record our daily lives and browsing habits, the addition of personal cloud computing gives applications the opportunity to acquire knowledge over time and predict what we need and want in real-time.
The first services that will be performed will generally revolve around simple tasks - such as creating a weekly to-do list or sending birthday messages. However, this type of activity outsourcing will eventually allow a greater array of applications and services to take control of other aspects of a user's life.
Before 2020, as cognizant computing develops to perform these tasks, data stored in the cloud will also allow devices to make sense of information gathered.
- more info
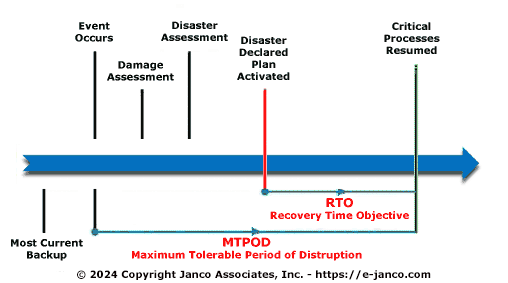
Backup infrastructure is critical in today's environment
Many companies are acutely aware of the costs and risks associated with lost or unrecoverable data on employee devices, including desktops, laptops, and mobile devices. While mobility initiatives, including bring your own device (BYOD), are gaining popularity, Janco Associates (www.e-janco.com) has discovered that many firms do not have adequate protection, recovery policies or tools in place to manage their ever-increasing volumes of data.
Janco believes there is a critical requirement to protect sensitive data residing on desktops, laptops, and mobile devices. It is more critical than ever, to have a a backup infrastructure in place along with formal BYOD procedures.
Must Have Policies
All of the policies that are provided here are contained within one or more of the templates that are on this site. These policies have been added as individual documents in WORD format (WORD 2003 and MS WORD) for those clients who just need this particular policy. All policies are Sarbanes-Oxley, HIPAA, PCI-DSS, and ISO compliant.
The policies have just been updated to comply with all mandated requirements and include electronic forms that can be Emailed, filled out completely on the computer, routed and stored electronically -- a total solution.
- more info
- CIO IT Infrastructure Policy Bundle (All of the policies below are included as individual MS Word files and a single PDF file. Electronic forms are all individual documents that are easily modifiable)
- Backup and Backup Retention Policy
- Blog and Personal Web Site Policy (Includes electronic Blog Compliance Agreement Form)
- BYOD Policy Template (Includes electronic BYOD Access and Use Agreement Form)
- Google Glass Policy (Includes Google Glass Access and Use Agreement Form)
- Incident Communication Plan Policy (Updated to include social networks as a communication path)
- Internet, e-Mail, Social Networking, Mobile Device, Electronic Communications, and Record Retention Policy (Includes 5 electronic forms to aid in the quick deployment of this policy)
- Mobile Device Access and Use Policy
- Patch Management Policy
- Outsourcing Policy
- Physical and Virtual Server Security Policy
- Record Management, Retention, and Destruction Policy
- Sensitive Information Policy (HIPAA Compliant and includes electronic Sensitive Information Policy Compliance Agreement Form)
- Service Level Agreement (SLA) Policy Template with Metrics
- Social Networking Policy (includes electronic form)
- Telecommuting Policy (includes 3 electronic forms to help to effectively manage work at home staff)
- Travel and Off-Site Meeting Policy
- IT Infrastructure Electronic Forms
Mobile Computing Digest - Summary of Current Articles
- more info
- Mobile Computing Top 10 trends for CIOs Mobile computing should be the focus of CIOs Every organization needs to identify and develop mobile computing security policies to be deployed which will provide...
- Mobile devices and BYOD drive CIO priorities Mobile devices and BYOD drive CIO priorities Mobile devices are becoming increasingly vital in the way we connect, engage, and understand our customers. But most...
- Top 10 security requirements for mobile user Top 10 security requirements CIOs need to address for mobile user CIO and IT Managers need to focus on more than convenience when considering mobile...
- BYOD security issues need to be addressed Seven BYOD security solutions As the use of BYOD increases, security is more of an issue and needs to be revisited frequently. Some of the...
- CIOs worry more about cyber threats with mobile computing Cyber threats are now a much greater concern with the expansion of the use of mobile devices and services. At the same time online criminals...
Best Practices Breifs
Best Practices for CIOs
- more info
- Social media policy needed to meet internal audit requirements Social Media Policy is Missing in Over 50% of all Organizations Internal audit has never been easy, and a recent survey shows that 43% of...
- 10 Compliance Best Practices 10 Corporate Compliance Best Practices Compliance is a major issue that organizations of all sizes need to address. In the information technology field they range...
- Top 10 Best Practices for BYOD Best practices for BYOD Janco has defined the following 10 best practices to follow as BYOD is implement. Have a BYOD policy in place before...
- 10 BYOD Best Practices for CIOs BYOD Best Practices for CIOs Bring Your Own Devices (BYOD) is exploding all over corporations. CIOs are in the cross hairs and need to follow...
- Top 10 Best Practices for Omni Commerce and ERP Omni Commerce and ERP top 10 best practices CIOs should follow As the new model Omni Commerce and its associated ERP solutions are implemented,...
Weak spending - a drag on IT Growth
Consumers spent more in March without raiding savings accounts, despite a smaller-than-expected bump in income, but the data still point to a slowly growing economy on the verge of stalling.
Spending climbed just 0.2% in March after a 0.7% surge in February, the Commerce Department said Monday. But that was better than forecasts for 0.1%.
Personal income also rose 0.2%, down from 1.1% in the prior month and below expectations for 0.4% growth. And while consumers didn't dip into rainy-day funds, they didn't add much to them either. The savings rate held at a modest 2.7%.
Lower gas prices probably helped households stay out of their savings accounts, said the president of Naroff Economic Advisors. But that's not a sustainable path to growth.
- more info
CIOs worry about SmartPhones becase they are full blown comuters
Smartphones are computers and have associated risks
The new era of smartphones and the Internet of Things can be a dangerous place to do business. It is enough to make a CIO long for the days when the biggest security threats were passwords written on sticky notes attached to computer monitors or the Stoned virus that made PC screens images jiggle.
While the new threats are real - although at times overblown as the white hat hacker economy depends on a questionable relation between hackers wanting to turn their digital cracking prowess into a business and vendors who want to keep bad publicity to a minimum - CIOs and corporate technology execs need to focus on the big security picture rather than sink into a morass of fixing every new vulnerability. Here are some lessons learned from attending this years Black Hat conference.
- more info
Mobility Policy Bundle (more info...) All of the policies below are included as individual MS Word files and a single PDF file. Electronic forms are all individual documents that are easily modifiable
- BYOD Policy Template (more info...) Includes electronic BYOD Access and Use Agreement Form
- Mobile Device Access and Use Policy (more info...)
- Record Management, Retention, and Destruction Policy (more info...)
- Social Networking Policy (more info...) Includes electronic form
- Telecommuting Policy (more info...) Includes 3 electronic forms to help to effectively manage work at home staff
- Travel and Off-Site Meeting Policy (more info...)
Twitter Timeline
Feedback requested on public transportation #pandemic planning guidance http://feedly.com/k/12TiSQ0 http://www.e-janco.com/Security.htm?utm_content=buffer15b59&utm_source=buffer&utm_medium=twitter&utm_campaign=Buffer #cio #security
CIO Daily News is out! http://news.e-janco.com
ICO hands out £200,000 fine for shocking NHS data breach http://feedly.com/k/15CH0Jf http://www.e-janco.com/Security.htm?utm_content=buffer03b37&utm_source=buffer&utm_medium=twitter&utm_campaign=Buffer #cio #security #compliance #janco
Data loss inevitable for half of businesses http://feedly.com/k/15CGVVR http://www.e-janco.com/Disaster_Recovery_Plan.htm?utm_content=buffer28fdd&utm_source=buffer&utm_medium=twitter&utm_campaign=Buffer #businesscontinuity #janco
Job Market wanes as budgeting for new year starts http://feedly.com/k/15CGOtk http://www.ejobdescription.com/CIO_Job_Description.html?utm_content=buffer7bdcd&utm_source=buffer&utm_medium=twitter&utm_campaign=Buffer #cio #career #janco #staffing
CIO Daily News is out! http://news.e-janco.com
CIOs need to get employees to engage to improve productivity http://feedly.com/k/15CGJpI http://www.e-janco.com/metrics_Book.htm?utm_content=bufferffb30&utm_source=buffer&utm_medium=twitter&utm_campaign=Buffer #productivity #budgets #janco
Cybercrime costs the US 500,000 jobs and billions http://bit.ly/14a4xOB #cio #disasterrecovery
Cybercrime costs the US 500,000 jobs and billion s http://wp.me/p2DNUr-qg
Robots That Can Aid In Disaster Recovery http://feedly.com/k/14zzWjB http://www.e-janco.com/Drp.htm?utm_content=bufferb6197&utm_source=buffer&utm_medium=twitter&utm_campaign=Buffer #disasterrecovery #janco
Company to help Navy improve how people, technology interact http://feedly.com/k/14npdZt http://www.e-janco.com/individual_policies.htm?utm_content=buffera1400&utm_source=buffer&utm_medium=twitter&utm_campaign=Buffer #infrastructure #policy #Janco
Tech hiring accounts for 10% of U.S. employment gains http://bit.ly/15U96Q1 http://bit.ly/15U95eW #cio #career #janco #staffing
CIO Daily News is out! http://news.e-janco.com
National Weather and Hazard Maps http://bit.ly/15XnEy9 http://bit.ly/15XnEyb #businesscontinuity #janco #disasterrecovery #weather
June Data Shows That IT Employment Soars http://bit.ly/12SpBNY http://bit.ly/12SpBO2 #cio #career #janco #staffing
Microsoft CFO: Reorganization Puts Us On The Right Track http://bit.ly/1dKlCEt http://bit.ly/1dKlCEv #productivity #budgets #janco
10 New Security Start-up Companies - IT Manager - CIO http://bit.ly/1dLQ2q7 http://bit.ly/1dLQ4hu #cio #security #compliance #janco
CIO Daily News is out! http://news.e-janco.com
- more info
Disaster Recovery Hot Topics
Current posts on disaster recovery and business continuity.- more info
- Disaster Recovery and Business Continuity Top 10 Disaster Recovery and business continuity are all about being ready for everything. The question that every IT manager and CIO has to answer every day...
- Options for a data center disaster recovery strategy Data Center disaster recovery strategy options A critical component of a disaster recovery business continuity is the data center disaster recovery strategy Hot...
- Sandy shows that not being prepared can be fatal to an enterprise Business Continuity Plans Are Expensive A companys disaster recovery and business continuity programs would be incomplete without covering compliance risks and without using compliance tools...
- High Availability Versus Disaster Recovery High Availability High Availability is when A machine that can immediately take over in case of a problem with the main machine with little down...
- Top 10 Selection Criteria for a Disaster Recovery Cloud Provider Cloud disaster recovery business continuity When looking for cloud providers of Disaster Recovery and Business Continuity Services you need to establish that they will be...
Cloud and BYOD Digest
Recent cloud and BYOD blog postings
- more info
- Many CIOs have not addressed cloud security issues Less than 50% of all organizations have policies in place that for vetting cloud computing applications for possible security risks before deploying them. The number...
- 10 BYOD Best Practices for CIOs BYOD Best Practices for CIOs Bring Your Own Devices (BYOD) is exploding all over corporations. CIOs are in the cross hairs and need to follow...
- Top 10 security requirements for mobile user Top 10 security requirements CIOs need to address for mobile user CIO and IT Managers need to focus on more than convenience when considering mobile...
- Released BYOD Policy Template Bring-Your-Own-Device BYOD Policy Template Janco has announced an update to the "BYOD Policy Template Bring-Your-Own-Device". BYOD Policy Template Includes an electronic form for employee agreement...
- Top 10 Mistakes on Mobile Devices and BYOD Top 10 mistakes that mobile users and IT support make With the move towards BYOD and mobile devices, some support responsibilities fall on users. These...
Mobile computing drives CIOs to focus on many compliance issues
Mobile devices let you do business any time and from almost anywhere. Share with colleagues from the beach, respond to a vendor from an airport, and close deals from commuter trains. But the enormous power of anywhere/anytime business comes with risks, especially if you work in a regulated industry or if your company is subject to corporate governance requirements.
Janco's Mobility Policy Bundle provides set of rules of the road that address issues like
- Best practices on usage of mobile devices including security compliance
- How to use social media compliantly on mobile devices
- Engaging effectively with your social connections
- How to untangle the complicated web of regulatory, legal, and corporate compliance requirements related to usage of mobile devices
- How the Mobility Policy Bundle helps you be compliant
Mobility Policy Bundle (more info...) All of the policies below are included as individual MS Word files and a single PDF file. Electronic forms are all individual documents that are easily modifiable
- more info
- BYOD Policy Template (more info...) Includes electronic BYOD Access and Use Agreement Form
- Mobile Device Access and Use Policy (more info...)
- Record Management, Retention, and Destruction Policy (more info...)
- Social Networking Policy (more info...) Includes electronic form
- Telecommuting Policy (more info...) Includes 3 electronic forms to help to effectively manage work at home staff
- Travel and Off-Site Meeting Policy (more info...)
Cybercrime watch
- more info
- Bank security weaknesses led to cyber looting of $45M from ATMs
- Payment card processors hacked in $45 million fraud
- Spamhaus DDoS suspect extradited to the Netherlands
- Accused SpyEye virus creator extradited to the U.S.
- Dutch bill would give police hacking powers
- DDoS suspect used a van as a mobile office, Spanish police say
- Dutch man arrested in connection with major DDoS attack on Spamhaus
- Australia charges man claiming to be LulzSec leader
- One in five data breaches are the result of cyberespionage, Verizon says
- Former LulzSec member gets prison sentence for Sony Pictures hack
Health IT funding is hot
Funding for health IT startups hit nearly $500 million during the first quarter of 2013, according to a new report from Mercom Capital Group, and the number of companies receiving funding more than doubled from last year.
Some of the areas getting funding include telehealth, mobile health and scheduling apps for patients
The most important aspect of any business is recruiting, selecting, and retaining top people. Research shows those organizations that spend more time recruiting high-caliber people earn 22% higher return to shareholders than their industry peers. However, most employers do a miserable job selecting people. Many companies rely on outdated and ineffective interviewing and hiring techniques. This critical responsibility sometimes gets the least emphasis.
- more info
IT Infrastructure key to productivity
With the explosion of technology into every facet of the day-to-day business environment there is a need to define an effective infrastructure to support operating environment; have a strategy for the deployment and technology; and clearly define responsibilities and accountabilities for the use and application of technology.
The IT staff at many businesses often spends a majority of its time on time-consuming lowvalue procedures and manual IT management tasks that keep the servers, network and storage running but detract from more strategic IT initiatives. Better tools for systems management can deliver automation and monitoring capabilities that reduce the amount of time needed manage the infrastructure and allow more time for the development and deployment of new applications and IT services that help grow the business.
Related posts:
- more info
- Top 10 Selection Criteria for a Disaster Recovery Cloud Provider Cloud disaster recovery business continuity When looking for cloud providers of Disaster Recovery and Business Continuity Services you need to establish that they will be...
- 10 steps to cloud disaster recovery planning Many companies now are including cloud disaster recovery process in their business continuity plans. Janco has found that disaster plans that include the cloud if...
- Options for a data center disaster recovery strategy Data Center disaster recovery strategy options A critical component of a disaster recovery business continuity is the data center disaster recovery strategy Hot...
- DRP BCP Best Practices Defined DRP BCP Best Practices Defined Here are some Disaster Recovery Business Continuity best practices Keep your primary backup disaster recovery business continuity data in...
- Disaster Recovery Plan in the cloud Paper disaster recovery and business continuity plans are difficult to keep up to date and be available for the recovery process. One solution that we...
Disaster recovery and business continuity have changed
Are your backup and DR challenges pulling you in different directions? Are virtual servers complicating your backup processes? Each area of data protection has its own set of challenges, particularly in terms of the cost and difficulty managing service levels (SLAs).
There is a solution to this problem the Janco Disaster Recovery Business Continuity Plan Template. It will guide you to go beyond outdated recovery techniques methods into the future.
- more info
BYOD - What you need to know
BYOD is now a reality for most enterprises. Some great resources for these are:
- more info
- BYOD Boosts Mobile Management Costs by Clint Boulton
- BYOD policies jacking up companies IT costs by Brad Reed
- When BYOD goes wrong by Darragh Delaney
Recent Blog Posts
- 10 BYOD Best Practices for CIOs BYOD Best Practices for CIOs Bring Your Own Devices (BYOD) is exploding all over corporations. CIOs are in the cross hairs and need to follow...
- Who owns a BYOD Issues on ownership of BYODs Organizations of all sizes face the legal question of who actually needs to own the device. Theres no clear answer...
- Released BYOD Policy Template - Bring-Your-Own-Device BYOD Policy Template Janco has announced an update to the BYOD Policy Template - Bring-Your-Own-Device. BYOD Policy Template Includes an electronic form for employee agreement...
- BYOD a reality - over 90% support them BYOD policies are a must With the advent of Bring-Your-Own-Device - BYOD and the ever increasing mandated requirements for record retention and security CIOs are...
- Mobile devices and BYOD drive CIO priorities Mobile devices and BYOD drive CIO priorities Mobile devices are becoming increasingly vital in the way we connect, engage, and understand our customers. But most...
CIOs face a security nightmare with the drive towards BYOD and cloud computing
High achieving employees typically want newer,faster and higher performance hardware than their employers provide for them across various platforms: desktop PCs, smartphones, and tablets. Often decisions about personal devices are not constrained by the return-on-investment and limited budget considerations that limit IT decision making.
The pervasiveness of BYOD is document many research studies:
- more info
- A Research and Markets study shows that 65% of enterprises worldwide have adopted BYOD to some extent by the end of 2012.
- An Aberdeen Group study shows that 75% of companies permit BYOD.
- Equanet says that 71% of tablets used in a business setting are employeeowned.
- Some companies are migrating to a completely BYOD approach, such as Cisco, where 100% of mobile devices are provided by employees and not the company itself.